
Welcome to our blog post, where we delve into the fascinating world of Mobile Ubiquitous Computing and its vital role in securing, managing, and controlling the ever-expanding universe of the Internet of Things (IoT). In this era of digital transformation, the IoT landscape is rapidly evolving, bringing about revolutionary changes in how we interact with technology in our daily lives.
Our journey today will explore how Mobile Ubiquitous Computing is not just a buzzword, but a critical solution addressing the complex challenges of IoT. We will unravel how this innovative approach seamlessly integrates computing capabilities into everyday objects, creating a network of interconnected devices that communicate with each other effortlessly.
The focus will be on the paramount importance of security in the IoT sphere. We’ll examine how Mobile Ubiquitous Computing implements robust security measures like advanced encryption, secure data protocols, and stringent authentication processes to safeguard against cyber threats and unauthorized access.
Data management is another key aspect we’ll explore. With IoT devices generating an enormous volume of data, managing this information efficiently is crucial. We’ll discuss how Mobile Ubiquitous Computing provides powerful tools for data analytics, cloud storage, and real-time processing, ensuring data is not just collected, but also intelligently utilized.
Control and automation form the crux of the IoT experience. This blog will shed light on how Mobile Ubiquitous Computing allows for effortless remote monitoring and management of devices, enhancing convenience and user experience through mobile applications, voice commands, and automated responses.
We’ll also touch upon the scalability and flexibility of these solutions. As IoT networks grow, Mobile Ubiquitous Computing is designed to scale and adapt, accommodating an increasing number of devices and diverse communication protocols.
Lastly, we’ll emphasize the user-centric approach of these solutions. In an IoT-driven world, the end-user experience is paramount. We’ll discuss how Mobile Ubiquitous Computing focuses on intuitive interaction, context-aware services, and personalized experiences.
So, join us as we embark on this enlightening journey through the realm of Mobile Ubiquitous Computing and its transformative impact on the IoT world. Whether you’re a tech enthusiast, an industry professional, or simply curious about the future of digital connectivity, this blog promises to offer valuable insights and exciting perspectives. Let’s dive in!
Table of Contents
1.2 An overview of the sector background to the topic. 6
1.2.1 Ubiquitous Mobile Background. 6
1.2.2 The technology in the ubiquitous computing. 7
1.2.4 Cyber security threats. 9
1.4 Objectives of the proposed title. 10
1.5 Summary of the project/case scenario) 11
2.2 Evolve of Ubiquitous Computing. 12
2.3 Internet of Things and Cyber security. 13
2.4 Ubiquitous computing and Internet of Things. 14
2.5 Architecture of Internet of Things. 14
2.5.1 Cyber security threats and vulnerabilities towards IoT devices. 15
2.6 Application areas of Pervasive computing. 16
2.7 How ubuquitous computing working. 20
2.9 Security vulnerabilities, threats in home automation(Smart home technology) 24
3 Proposed Methodology and proposed design to your mobile application. 30
3.2 methodology of carrying out the project interviews( questionnaires) 34
3.2.1 DESCRIPTIVE QUESTIONS –. 34
3.2.2 MULTIPLE CHOICE QUESTIONS – 36
3.3 questionnaires/secondary data (referring Internet Resources) 37
3.4 interface design to get information anywhere and any place. 39
3.4.3 DEFAULT DEVICE SCREEN.. 41
3.4.4 Out Traffic Interface. 42
4 Discussion of the proposed Mobile Ubiquitous Computing solution. 44
5 Conclusions and recommendations. 47
5.2 Recommendations To Smart Homeowners. 50
1 Introduction
1.1 Introduction
The purpose of Mobile Ubiquitous computing solutions is to develop a computing environment where users can interact and access services, data, and information at any time and from any location while using any device. This covers everything from wearable technology, sensors and other IoT devices to smartphones and tablets.
To ensure that data is secure, effective, and managed, Mobile Ubiquitous Computing Solutions leverage a variety of technologies, including virtual private networks, mobile device management, identity and access management, and data encryption. This aids organizations in enhancing overall user experience, increases in productivity, and operational efficiency.
The field of Mobile Ubiquitous Computing Solutions are dramatically evolving and is transforming how we interact with technology. Mobile Ubiquitous Computing Solutions will become more crucial in facilitating seamless connectivity and offering a secure and effective computing environment as more devices and services are interconnected.
This chapter investigates technical aspects of the Mobile Ubiquitous computing solution to secure, manage and control the information of smart homes.
As more individuals adopt Internet of Things (IoT) devices like smart thermostats, security cameras, and lighting systems, smart homes are growing in popularity.
However, these devices can also pose security risks, as they are often connected to the internet and can be vulnerable to hacking and data breaches. Mobile Ubiquitous Computing Solutions can provide an efficient, effective, and secure way to manage and control the information generated by smart home devices.
If we discuss about the array of this report, after having the background knowledge on the meaning of ubiquitous mobile computing then it will move to the IoT background where it will describe about an overview of the sector background to the problem.
Problem statement describe about the solutions of mobile ubiquitous computing that we can use to secure, manage, and control information of Internet of Things. In addition to that, this piece of literature is highlighted the point that there are cyber-attacks for IoT devices. So that it is essential to implement mobile ubiquitous computing solution to prevent those cyber-attacks.
Objectives are mainly based on mobile ubiquitous computing solutions and the IoT devices. Securing the IoT devices in terms of the mobile ubiquitous computing and simultaneously solutions for real world problem with the evolve of new technologies and devices summarized by this sector.
Literature review is interweaved by mobile ubiquitous computing, IoT devices and the cyber security concepts. Proposed methodology and the proposed design application thoroughly described in accordance with the new advancements.
Discussion is an analysis on current mobile ubiquitous computing solutions and the proposed mobile ubiquitous computing solutions.
Conclusion is the comprehensive discussion of the mobile ubiquitous solutions used to secure the smart home technology and the recommendations are based on in comparison of the prevailing mobile ubiquitous computing solutions and the proposed solution. Improvements for the discussed solution are addressed in my recommendations.
1.2 An overview of the sector background to the topic.
According to [1] [4], there were 26.66 billion active IoT devices. In the year 2020, it was expected to have 31 billion IoT devices. Also, it is expected to have 75 billion IoT devices by 2025. According to the above statistical data, we can conclude that IoT security and energy efficiency of IoT is essential.
Due to the less computational power in IoT devices, it is not easy to have high energy and resource consuming programs running in the IoT devices. Therefore, we need to implement lightweight application IoT devices to strengthen security and efficiency.
among all IoT technologies, smart homes are very popular in the present technological world. The best solution to ensure the security of IoT devices can be accomplished through ubiquitous mobile computing technologies.
After identifying the primary security goals, confidentiality, integrity, authentication and authorization, availability, accountability, auditing, non-repudiation, and privacy goals we can succeed in implementation of effective and efficient IoT security.
To address these IoT security issues, we must develop security solutions that leverage low overhead protocols and high computational techniques with cost reductions to give strong encryption and authentication to IoT devices.
1.2.1 Ubiquitous Mobile Background
What is ubiquitous mobile computing?
ubiquitous computing also known as Pervasive computing, involves embedding connectivity features into all the objects present in our surroundings, enabling them to automate regular tasks, communicate with each other and minimize human effort required to perform tasks and follow machine commands.
Pervasive computing, which is also known as ubiquitous computing, is a developing movement that involves integrating computer power (usually through microprocessors) into common objects, so they can communicate and carry out beneficial tasks without requiring users to interact with them as conventional computers. These pervasive computing devices are linked to networks and always remain readily accessible.[7] [2]
1.2.2 The technology in the ubiquitous computing.
Applications for ubiquitous computing have been created for consumer usage and to assist individuals in their social interactions and regular activities.
An Apple Watch that alerts the user to a phone call and enables the user to answer the call through the watch is an explication of pervasive computing. Another situation is when a subscriber to Audible, Amazon’s audio book server, begins their book on the train using the Audible app on a smartphone and continues using it at home using an Amazon Echo.
An environment in which devices are available everywhere, are capable of some form of computing can be considered as an environment with ubiquitous computing.
since pervasive computing systems capable of gathering, analyzing , and transmit information, they can adapt to the data context and data activities. That is, a network that can comprehend its environment and improve human experience and quality of life.
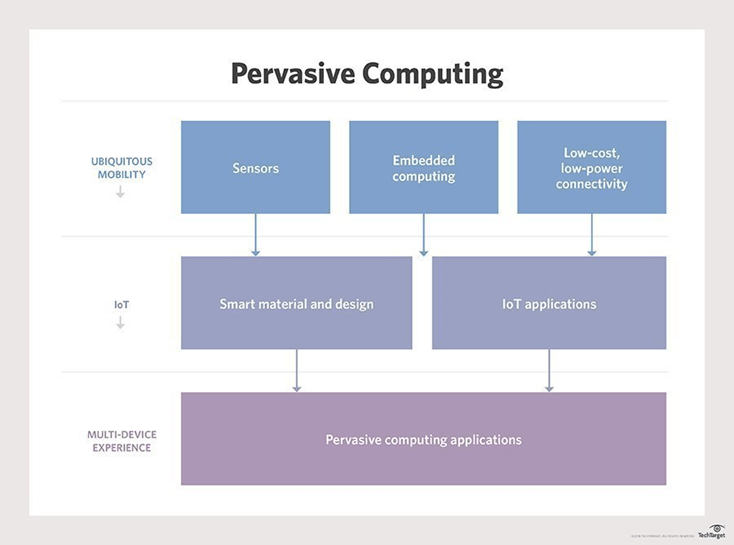
Figure 01 : This figure of pervasive computing shows the role of sensors and other low-power embedded devices in ubiquitous computing[7] [2]
1.2.3 IoT Background
What is meant by IoT devices?
IoT stands for the Internet of things. In general, there are many definitions for the technology of Internet of Things. The IoT system can be described as a system equipped with computing devices, mechanical devices, or provided with unique identifiers, and IoT systems can transmit and communicate without human interaction. A “thing” can be a sensor or a biochip transponder, or any other mechanical device, and that object is assigned to a MAC Address and an IP address to transmit data over the network [2] [2].
Any mechanical equipment which can contribute to the smart sensor technology can be categorized as an IoT environment. The Internet of Things is a technology combining multiple devices which can turn on and off the web to enable automation and use software to enhance smart living[3] [3]
IoT devices can be described as a network of physical devices interconnected via the Internet of any source of the network. These physical devices can be in many forms of devices. Tablets, smartphones, smart TVs, wearable smart devices, and smart car appliances can also be categorized as IoT devices. Therefore, in our day-to-day life, we will experience the use of many IoT devices in many forms. Figure1 shows appliances of IoT devices [4] [1].
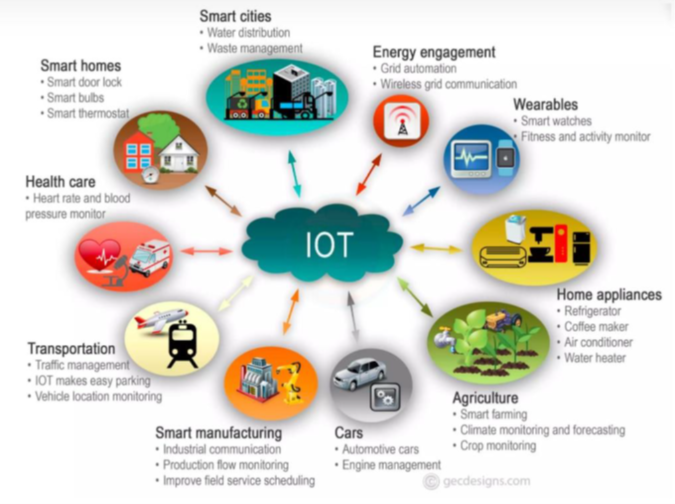
Figure 02: IoT appliances and their application areas [4] [1]
1.2.4 Cyber security threats
There is a plethora of vulnerabilies in IoT devices. Because cyber-attacks against IoT devices are not advanced and easy to implement and perform, hackers frequently execute them out in order to capture sensitive data and information.
The majority of IoT security threats can lead to information leakage and service disruptions. These security hazards may potentially pose physical security threats and risks that are dangerous to individuals.
Cybersecurity threats represent the possibility of a cyberattack. A cyberattack is a deliberate and hostile attempt by one organization or individual to compromise the systems of another individual or organization. The attacker’s motivations might include financial gain, data theft, sabotage, or espionage.
There are some main type of cybersecurity threats which we can address through ubiquitous computing such as password attacks, man-in-the-middle attack(MitM), advanced persistent threats(APT), distributed denial of service(DDoS), software supply chain attacks
1.3 Problem Statement
In a smart home there are many IoT appliances. As an example, smart door lock, sensors etc. The computational power in these devices is very low. Due to this reason, the ability to defend against cyber-attacks is significantly reduced. This brings us to think about the security of these IoT devices that are connected to the home network. Due to the lack of resources, cyber criminals can target these IoT devices and can gain access to the network. To counter this problem, we need to increase the security of the IOT device. There for having a safe mobile ubiquitous system is important to the safety and privacy of the home network or to the smart home.
1.4 Objectives of the proposed title.
The objective of this proposed research is to secure the smart home device which is mainly under IoT devices. In order to do that we are going to implement a security firewall to secure the smart home appliances. The proposed firewall can actively monitor the in and out on network traffic which goes to these IoT devices. If there is any threat detected, then the proposed system can notify the users and take appropriate action to secure the network and data.
Addressing and Enhancing IoT security through mobile ubiquitous computing and improving energy-efficiency are the research goals. The objectives are to build an enhanced firewall to increase the security of web servers by using mobile ubiquitous computing solutions on IoT devices by using an energy-efficient methods and performance-oriented firewall that replace traditional firewalls. Making the firewall and web server applications better and more environmentally friendly is also an important goal.
1.5 Summary of the project/case scenario)
Internet of Things (IoT) devices are incrementally becoming ubiquitous, as are IoT services. Their achievement has not gone undetected, and the number of threats and cyberattacks against IoT devices and services is also escalating.(01) [4]
This research aims to identify security vulnerabilities and threats In IoT devices and provide solutions in terms of Mobile ubiquitous systems and mitigate the security issues after identifying main issues related to the security of IoT devices and services.
2 Literature Review
2.1 Pervasive Computing
Ubiquitous computing is considered as a rapidly evolving application of information and communications technology which is more incorporated in to regular activities than ever before, rather than as a discrete sector of technology Through the ubiquity of ICT systems, the objective is to achieve the claim of “everything, always, everywhere” for data processing and transferring.[9] [5]
Layers of ubiquitous computing
It is not as simply as innovating a new type of computer with varying abilities from its predecessors to define pervasive computing. It’s as difficult as developing a new way of engaging with and acquiring information, interacting, and living. Wireless sensor networks can be used in conjunction with the Internet of Things (IoT)[3] [6]
Such sensor networks acquire data from specific device sensors before transmitting it to an IoT server. Consider a system of layers with a specified set of tasks that align together to form pervasive computing. These layers consist below characteristics:
The Task Management layer investigates user tasks, context, and indexes. It also manages the territory’s complex interdependencies.
The Environment Management layer keeps track of resources and their capabilities, as well as mapping service requirements and user-level statuses of specific capabilities.
The Environment layer manages the important resources and manages their dependability.[8] [7]
2.2 Evolve of Ubiquitous Computing.
The origin of ubiquitous computing happened on late 1980s, ubiquitous computing” was coined in 1988 by Mark Weiser, CTO at Xerox PARC (or the Palo Alto Research Center). He co-authored some of the first studies on the subject alongside John Seely Brown, chief scientist, and director of PARC. Weiser is credited for coining the term “ubiquitous computing” and diving into its underlying difficulties. [3] [6]
Mark Weiser, former Scientific Director of the Xerox Palo Alto Research Center, shaped the concept of ubiquitous computing as an omnipresent infrastructure for ICTs as early as 1991.His work on ubiquitous computing continues to define all technological and sociopolitical aspects of the field. According to Weiser, ubiquitous computing can be categorized under the four criteria listed below are met: (i)Microcomputers are integrated into physical objects of any shape, displacing services previously performed by desktop systems; (ii) these embedded systems are distinguished by their small size and near invisibility to the user; (iii) embedded microcomputers thus augment a physical object’s original use-value with a new array of digital applications; and (iv) the ubiquitous availability of service lists at the heart of communication between systems and devices[9]. [5]
This last phase distinguishes ubiquitous computing from today’s common mobile networks. Ubiquitous computing is defined by the ubiquitous and mobile availability of services, regardless of the target platform. Services will be adapted to a Ubiquitous Computing device’s physical capacity. Applications Challenges and Future Trends specific device, whether a mobile telephone, PDA, or other value-added communications device [4] [1]
2.3 Internet of Things and Cyber security
With the evolution of the Internet of Things, cybersecurity has become a significant concern in the recent world. The purpose of using IoT devices is to store [8] [10]sensitive data. With the rapid increase of cyber-attacks, safe holding of sensitive data became a critical task for IT Infrastructure. IoT devices are equipped with limited resources. Most of these IoT devices are sensors that are low-powered and low computer resources. Therefore, IoT devices do not support strong encryption mechanism [9][11]. It is important to have a reliable encryption protocol to increase the privacy of data. With these low-security conditions, an attacker can interpret the communication between two parties. According to [9][11], the authors learned that all commercial solutions were expensive. And not openly accessible to everyone. Due to this reason, it is needed to have a security-enhanced firewall. The configured firewall has the following features that can mitigate the most recognized attacks. Enable ipv4 masquerading which device was acting as a Source-NAT gateway. Enabled spoof protection can verify the source addresses. Avoiding ICMP redirects to mitigate the MITM attacks [9] [11]. The main issue in this implication is that the efficiency and the power consumption were high. Because of this implication, we need to use multiple protocols and in-built applications.
As later discussed, three key problems related to IoT devices, data confidentiality, privacy and trust can be explained below.
Data confidentiality is a significant issue with IoT devices and services. In IoT context not only user may access data but also authorized object. [10][6] The IoT device needs to verify that an authorized entity is authorized to access a service through two mechanisms: access control and authorization and authentication and identity management (IDM). [10][6]
Because of the ubiquitousness of the IoT environment, privacy is a key concern in IoT devices and services. Because entities are interconnected and information is transmitted and distributed over the internet, user privacy has become a significant subject in many study efforts. Privacy in data collecting, data sharing and management, and data security challenges remain unresolved research issues.[10] [11]
Trust plays a significant role in establishing secure communication when several things communicate in an uncertain IoT environment. Two dimensions of trust should be considered in IoT: trust in the interactions between entities, and trust in the system from the user’s perspective [10] [11]
2.4 Ubiquitous computing and Internet of Things.
The internet of things (IoT) arose largely evolved from pervasive computing. While others claim that there is little or no difference, IoT is more in line to be associated with pervasive computing than Weiser’s first notion of ubiquitous computing. [7] [2]
As in ubiquitous computing, IoT-connected devices communicate and convey alerts or notifications about usage. The vision of pervasive computing is computing power widely distributed throughout the day today living in everyday objects. IoT is on its way to providing this vision and transforming mundane objects into interconnected devices, but it now requires a significant amount of configuration and human-computer interaction, which Weiser’s ubiquitous computing does not require.
Wireless sensor networks may be applied to IoT. These sensor networks gather information and data from individual sensors on devices before transmitting it to an IoT server. When gathering information on how much water is leaking from a city’s water mains, it might be advantageous to first collect data from the wireless sensor network. In some circumstances, as an example, wearable computing devices, such as an Apple Watch, data gathering and processing should be transferred immediately to an internet server where computing technology is centralized.[7] [2]
2.5 Architecture of Internet of Things.
Hui Suo et al. mention that IoT extends the definition of the term “internet” by incorporating corresponding technologies such as traditional Internet, mobile networks, sensor networks, and so on. Every “thing” is interconnected to the “Internet,” and all of these “things” communicate with one another.[12] [12]
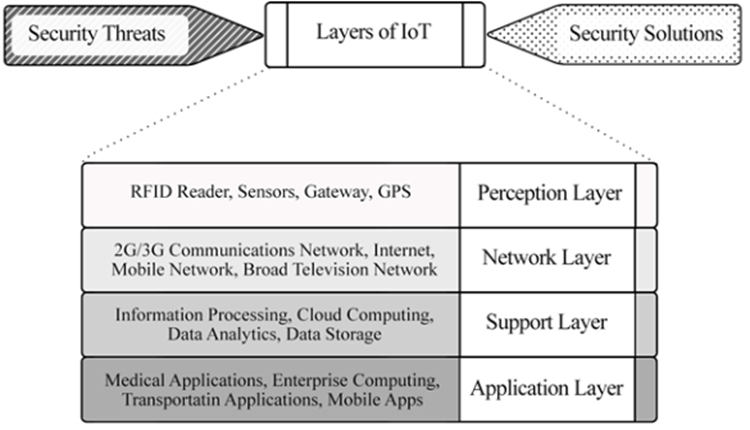
Figure 03: Architecture of Internet of Things[13] [13]
The architecture of Internet of Things is mainly depending on four categories under application, support, network, and perception layers.
2.5.1 Cyber security threats and vulnerabilities towards IoT devices
In addition to these IoT security vulnerabilities can allow many malevolent hackers to obtain our personal information for their own gain by exploiting the weaknesses of IoT systems. This section will address the several types of cybersecurity threats against IoT systems. [14] [14]
| Categorization | Cyber Security threats or Attacks | Security Impacts |
| Physical Attacks | Analysis of side channels, Node tempering, Radio frequency jamming | These vulnerabilities will allow attackers to manipulate node or sensor data and physically destroy IoT hardware. |
| Z-Wave Attacks | Z-Wave downgrade attack, Z-Wave injection attack, Z-Wave Man in the middle attack | These assaults will enable hackers to implement out security attacks on Z-Wave devices. |
| Network Attacks | traffic analysis attack, Selective forwarding, Sybil attack, Sinkhole attack, Botnet attack, Hello-flood attack, Man in the middle attack | These exploits will allow hackers obtain remote access and transmit incorrect instructions to IoT devices, allowing them to seize control. |
| Application Attacks | Code injection, Buffer overflow, SQL injection, Session Hijacking, Authentication and Authorization attacks | By obtaining unauthorized access to the IoT application level, hackers will be able to steal sensitive data. |
| Zigbee Attacks | Eavesdropping attack, Replay attack, Packet forging attacks. | These techniques will enable an attacker to acquire sensitive data and Zigbee traffic. |
Table 01 : several types of cybersecurity threats against IoT systems[14] [14]
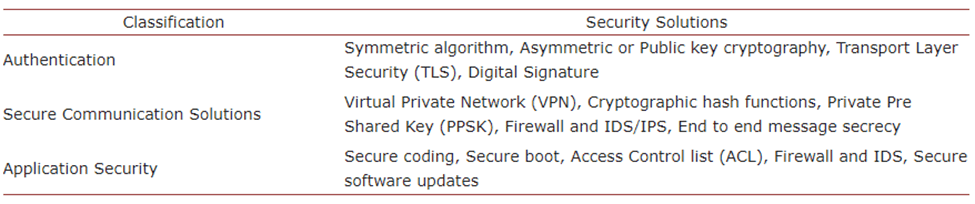
Table 02: security solutions for cybersecurity threats towards IoT systems[14]. [14]

Table 03: Ways to fulfil Security requirements[13] [13]
2.6 Application areas of Pervasive computing.
Ubiquitous computing intends to penetrate and integrate all aspects of life, enabling a ubiquitous flow of data, information, and, in the future, knowledge, through incorporating cognitive capabilities. With ubiquitous computing systems, a large variety of electronic devices are compatible. Let’s explore the most common application areas of ubiquitous computing in this chapter. Ubiquitous computing envisions a future in which small, potentially portable gadgets, sensors, and actuators communicate with one another. Pervasive computing has various potential applications, including environmental monitoring, health and home care, and intelligent transportation systems. Among the numerous applications are the following[3] [6]
Logistics
Tracking logistical commodities along the whole transit chain of raw materials, semi-finished products, and finished products (including their eventual disposal) bridges the gap in IT management systems between physical and information flow. This provides the opportunity to automate and streamline existing logistics. Sensor technology can be used by computers to gather, define, and evaluate factual information. Users must convert the data into a higher-level concept known as a “scenario.”[9] [5]
Motor traffic
Automobiles already have a numerous sophisticated assistance technologies that assist the driver discretely. Vehicles will be networked with one other and with surrounding telematics systems are anticipated for the future[9] [5]
Self-driving vehicles
It is also an amazing application of ubiquitous computing expertise. The structure is intended to respond autonomously to transmitted information, either reactively, through basic monitoring, or proactively. The system is designed to provide an in-vehicle system that assists the driver with travel planning (drive panel), provides a comfortable environment for the driver whilst observing him (wellness panel), and controls interactions with their mobile phone and the digital world adaptively[3] [6]
Military and armed forces sector
The military sector requires as extensive, multidimensional, and interrelated knowledge on avoiding and combating potential hazards as possible. This includes gathering and processing information. It also includes the development of new armament systems.
Several fights in the twenty-first century will necessitate the deployment of ubiquitous computer and network technology in military defense. Furthermore, these strategies can improve strategic abilities such as detecting and sensing, exchanging, and sharing sophisticated real-time data, and reinforcing the capability of strategic units[9] [5]
Home Automation
There are several smart home gadgets available, and the number will only increase as home automation becomes more popular. Smart bulbs, smart locks for windows, doors and cupboards – we’re only just beginning to understand how technology may change our lives. In addition to lighting, home automation systems can control temperatures, entertainment, and other digital or electrical appliances.
Ubiquitous computing can thus turn numerous home technical systems, such as heating, lighting, ventilation, and communication equipment, into intelligent objects that respond to tenants’ demands automatically. Ubiquitous computing enables the automation of daily physical duties, relieving us of all manual labor within the household and allowing us to live more comfortably and freely.
The use of these technologies tends to change our traditional perceptions of time and place, liberating us from the constraints imposed by the physical bounds of the in the home. Smart home technologies may simply make daily tasks easier, in addition to the benefits provided by electrical and mechanical technology[3] [6]
Production firms
The flow and processing of components throughout manufacturing are controlled by the components as well as the processing and transport stations themselves in the smart factory. Ubiquitous computing will enable a decentralized manufacturing system capable of self-configuring, controlling, and monitoring.[9] [5]
E-commerce
Smart objects enabled by ubiquitous computing encourage the development of new business models by utilizing a wide range of digital services. This comprises location-based services, the transition from purchasing to renting items, and software agents which will train ubiquitous computing components to operate as services and business operations on their own.
Smart services in today’s business world react to evolving market conditions. When market conditions vary, so should the design of smart service devices. This aspect of adaptation in smart gadget development has inherent challenges that may hinder the device’s service quality. Yet, the advantages exceed the minor drawbacks associated with implementing and administering smart gadgets[9]. [5]
Medical technology
As pervasive computing becomes increasingly autonomous, adaptable, smaller, and interconnected, medical applications, such as smart implants, present many alternatives for monitoring the health of the ill and elderly in their homes.Because ubiquitous computing integrates well with a wide range of applications, it may be of particular importance.
Ubiquitous technology is already enabling the development and administration of individualized health and wellness services that intelligently respond to and adapt to clients’ ever-changing needs. This field deals with a wide range of concerns, including but not constrained to disease monitoring, support diagnosis, behavior counseling, and others[3] [6]
National Security
Identification gadgets, such as electronic passports and smart cards, are examples of pervasive computing applications in internal security. Monitoring devices will become increasingly important in the long run, for example, in environmental protection and the surveillance of essential infrastructure, such as airports and power grids.[3] [6]
2.7 How ubiquitous computing working

Figure 03: How ubiquitous computing works[3] [6]
Technology in MUC
Ubiquitous computing is not an independent concept. Instead, it defines the performance qualities of a method for invisibly, ubiquitously, and seamlessly communicating information and communication. As a result, a smart object cannot be defined in general terms because so much depends on the context of its application: it may be an autonomous, compact, mobile gadget[9] [5]
A smart item could be integrated into a residence, or a domestic device could be converted into a smart object by integrating the necessary components. This diversity demonstrates that the technological foundation of ubiquitous computing is not always the same.
Table 1 does not reveal the relative importance of each field. Microelectronics, for example, is a prerequisite for any type of electronic data processing. Nevertheless, Table 1 defines it as necessary for two characteristics: mobility and embeddedness. It does not, however, represent the fact that mobility is a major component of ubiquitous computing, implying that microelectronics is given more weight[9] [5]
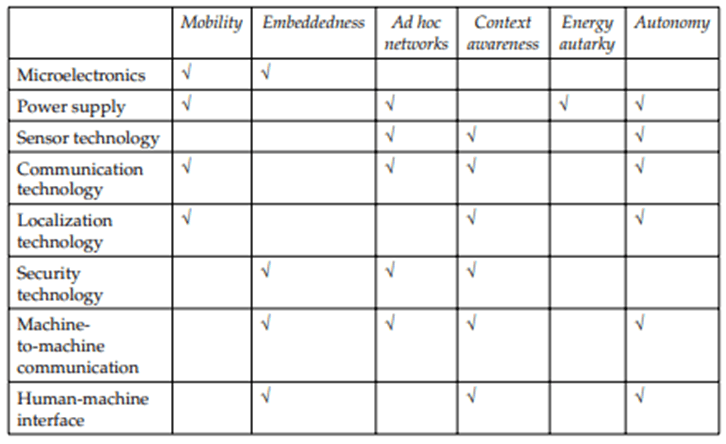
Table 01: Technologies required for ubiquitous computing [9] [5]
Microelectronics
Microelectronics, which deals with the miniaturization, development, manufacturing, and application of integrated circuits (IC), is already an important component in a wide range of technological gadgets and equipment that form modern life[9] [5]
Sensor technology
One of the key properties of ubiquitous computing is the ability to capture and analyze real-world data. At the heart of this is the sensor, which is an electrical component that registers qualitative or quantitative environmental parameters and amplifies, analyses, and relays them as a digital output. Today’s key challenges in sensor development include reducing the size and weight of sensors and sensor systems, interconnecting sensors into complex semiconductor systems, lowering sensor power consumption, improving sensor performance and reliability, and developing lower-cost manufacturing technologies [9] [5]
Communication technology
To emphasize the overlap between the two fields, communication technology is commonly paired with information technology and referred to collectively as ICT. In the field of telecommunications, telephony and satellite communication, mobile communication – radio engineering, communications engineering, signal transmission technology, switching technology, microelectronics, high frequency engineering, communication networks and technical informatics are important subfields [9] [5]
Localization technology
One intriguing aspect of ubiquitous computing is the ability to precisely localize smart objects by providing them with proper transmitters and receivers. Location-based services provide services depending on the users’ geographic locations. The employment of proper localization technology is an absolute requirement for the delivery of these services. Three main types of localizing technologies are, cellular supported, satellite supported and indoor localization systems [9] [5]
Security technology
The capability of virtually all smart items to exchange information is a key feature of ubiquitous computing. So, security is critical in ubiquitous computing. The fact that most communications in ubiquitous computing is wireless increases the importance of security because radio transmission is more easily manipulated [9] [5]
Machine to machine communication.
The capability of virtually all smart items to exchange information is a key feature of ubiquitous computing. So, security is critical in ubiquitous computing. The fact that most communications in ubiquitous computing is wireless increases the importance of security because radio transmission is more easily manipulated [9] [5]
Data Privacy
The purpose of data protection is to secure an individual’s privacy. Data security is more important in ubiquitous computing than in traditional information systems. The enormous number of smart objects, as well as their spontaneous networking, compromise the overall system’s controllability [9] [5]
Human machine interface
The smart devices of ubiquitous computing required the development of user interfaces that go beyond the previously dominating monitor/keyboard approach. Most objects will have several interfaces to their surroundings, but none of them will incorporate visualization components. Also, to avoid populating the user with information, there will be many implicit interactions in which the user has little or no input in the computing process. Yet, the user must be able to control the operations of ubiquitous computing via an acceptable human-machine interface.[9] [5]
2.8 Mobile Ubiquitous Computing Solutions to Secure, Manage and Control information of Internet of Things (IoT)
Mobile Ubiquitous Computing Solutions (MUCS) is a term to describe a set of technologies and methodologies that allow mobile devices to be seamlessly integrated with Internet of Things (IoT) devices. The purpose of MUCS is to provide a secure, efficient, and effective method for managing and controlling the data and information generated by IoT devices.
Mobile Ubiquitous Computing Solutions accomplishes this goal by combining numerous critical technologies and methodologies, including:
Mobile device management (MDM) is a technology which enables organizations to secure and manage mobile devices such as tablets and smartphones from a centralized dashboard. To prevent unwanted access to sensitive data, MDM can be used to impose security regulations such as password restrictions and remote device wiping.
Enterprise mobility management (EMM): EMM is a comprehensive approach to mobile device management that incorporates MDM as well as other additional tools for controlling apps, data, and content on those devices. EMM can be used to affirm that mobile devices are correctly configured and secure, as well as to manage data flow between IoT and mobile devices.
Identity and access management (IAM): IAM is a collection of technologies and processes which used to manage user identities and resource access. Organizations can use IAM to ensure that only authorized people have access to IoT devices and the data and information they generate.
Virtual private network (VPN): A VPN is a technology that establishes a secure and encrypted connection between two devices over the internet. VPNs can be used to securely interconnect mobile devices to IoT devices, by ensuring that data is secured from unauthorized access .
Data encryption: Encrypting data is a technique of protecting data by transforming it into a code that can only be deciphered with a secret key which is also known as an encryption key. Organizations may ensure that data generated by IoT devices is secured from unauthorized access even if it is intercepted in transit by encrypting the data.
Mobile Ubiquitous Computing Solutions is capable of offering a comprehensive solution for securing, managing, and controlling the information and data generated by IoT devices by combining various technologies and techniques. This can assist organizations in safeguarding sensitive data and ensuring that only authorized individuals have access to it.
2.9 Security vulnerabilities, threats in home automation(Smart home technology)
Prevailing vulnerabilities, poor configuration, and utilizing default passwords are just a few of the things that may allow a hacker to compromise at least one device in a smart home system. Once a single device has been infiltrated, hackers can execute a variety of actions based on the device’s capabilities and operations. Some of them are illustrated here.
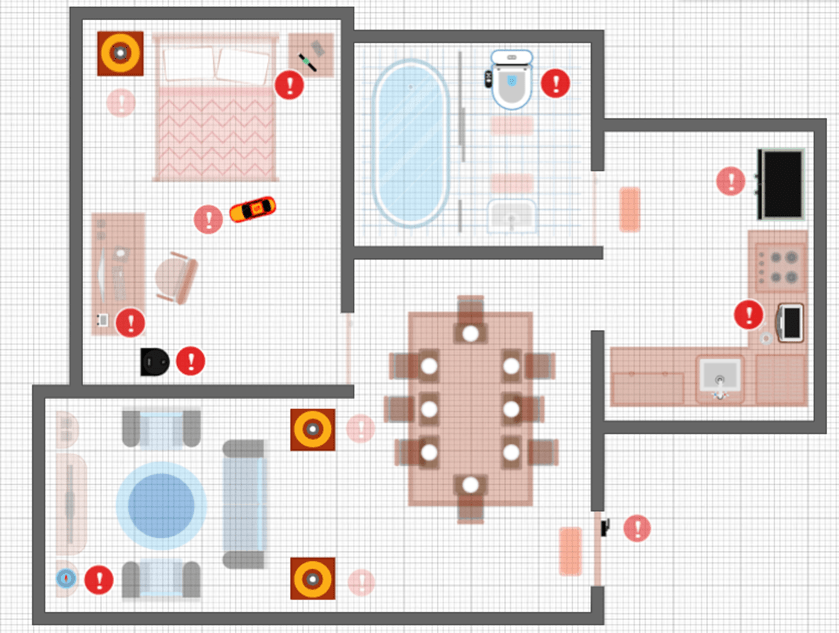
Figure 04: A home automation system with vulnerable devices and threats[11] [15]
The red warning symbols indicate the devices which are vulnerable to a cyber-attack. A failure or an invasion of one of the above devices allows to obtain the complete access or the control of the smart home. [15]
In the entering, smart lock allows hackers to control who comes in and out of the house. The most obvious option for hackers is to enable intruders or collaborators into the property, while another is to lock out the genuine residents. Hackers can get unauthorized access to smart home equipment like security cameras and door locks and use them to spy on people or gain entry to the home[11]. [15]
Smart bulbs can be everywhere in the house, they can be installed externally or internally. These can be switched on or off according to the time of the day, the amount of movement detected, or the quantity of ambient light sensed. Nevertheless, hackers can utilize these seemingly basic devices to disrupt homeowners, for example, by turning them on at inconvenient times[11]. [15]
Depending on the hacked device, specific individuals of the household may also be targeted. Compromise smart devices represent a special concern to children. Attackers can, as example, directly connect with the child or silently record the child’s behavior while playing with the toy. Vulnerable smart toys demonstrate how even devices that are safe for children can do harm if they are corrupted[11]. [15]
The point at which smart devices are integrated can potentially be valuable to hackers. Hackers can take advantage of the home gateway to reroute or change connections. This proves that everything connected to the smart home network can be just as beneficial to an experienced hacker as it is to the house owner[11]. [15]
Several different devices can be installed in the living room. A smart speaker, for example, can serve as an intermediary for voice-initiated home automation commands. A voice-activated sensor, such as a smart speaker, can allow hackers to give their own voice instructions. They can play their own voice commands or thieve voice data to use as credentials for other voice command systems[11]. [15]
Smart robot vacuum cleaners, which can navigate around the house, can give intruders with information on the home’s layout. The hackers might use this information to plan future operations and moves.
Smart technologies are increasingly available in the bathroom, most notably in the form of smart toilets. A smart toilet includes several functions, such as sensing the appropriate amount of water to flush waste, that can be very useful to consumers. However, hackers can exploit some of its functions to cause the device to malfunction, such as making the toilet flush continually or allowing water to run continually from the bidet[11]. [15]
If successfully hacked, smart refrigerators and coffee makers in the kitchen can cause major problems. Hackers can program a smart refrigerator to enter incorrect expiration dates or order massive quantities of supplies online. Even a smart coffee maker can be extremely inconvenient if hackers instruct it to brew coffee indefinitely[11]. [15]
wearable and portable smart gadgets add another level of complexity to IoT security problems because they operate in both enterprise and home environments, and they have even prompted changes to many companies’ “bring your own device” (BYOD) rules. Users usually bring these devices, including as smartwatches and smart yoga mats, to the office and then bring them home at the completion of the workday. A malware infestation discovered in a contained environment, For example, if BYOD regulations are weak or adequate security precautions are not implemented to avoid such a vulnerability, it can spread to the other.[11] [15]
Furthermore, as more individuals utilize Internet of Things (IoT) technologies such as smart thermostats, security cameras, and lighting systems, smart homes are becoming more popular. Nevertheless, because these gadgets are frequently connected to the internet, they can be vulnerable to hacking and cyber-attacks. Cyber assaults on smart homes pose the following risks:
Unauthorized Access: Hackers can get unauthorized access to smart home equipment like security cameras and door locks and use them to spy on people or gain entry to the home.
Data theft: Smart home gadgets can generate an immense amount of sensitive data, such as video footage or personal information, which can be acquired during a cyber assault.
Malware: Hackers can install malware on smart home devices to steal data or launch additional assaults.
Distributed denial of service (DDoS) attacks: Smart home devices can be exploited as part of a botnet in a DDoS assault, which can overwhelm networks and websites.
Physical destruction: In some situations, cyber-attacks on smart home equipment can lead to physical damage, such as shutting down the heating system in the middle of winter or triggering a fire.
Privacy violations: Smart home gadgets can be used to monitor activities in the home, and a cyber-attack could lead to the release of personal information or privacy violations.
in conclusion, because of their internet connectivity and the sensitive data they generate, smart homes can be subject to cyber-attacks. To mitigate these threats, smart homes should use strong security methods such as difficult passwords, keeping software up to date, and implementing Mobile Ubiquitous Computing Solutions (MUCS) to secure, manage, and govern their data.
2.10 Related work
The rapid increase in consumption of the IoT device created new challenges and new opportunities. Also, most IoT devices are becoming highly mobile, and it can be difficult to contact them via Just IP address. A two-way communication firewall was essential to address these issues in IoT devices[12] [16]. All the IoT devices do not follow only one protocol to communicate with other devices. Different IoT devices have Differentiated operating systems and different protocols to share with them. Due to this reason, one universal message communication protocol is necessary to communicate with other devices in the network [12] [16].
A firewall can be software or a combination of software and hardware. Also, we can add firewall policies to the firewall to govern the network traffic between two or more nodes. Therefore, the performance of the firewall is significant. When the system is going through any kind of attack, it is vital to have an efficient firewall. The current firewall’s inability to adapt to new attacks is a significant security concern. Most firewalls cannot analyze traffic characteristics such as destination IP address and source IP address. Also, available firewalls for IoT do not support anomaly detection and countermeasure techniques to avoid being attacked. [5] [17] Therefore to improve the security of IoT devices, it is necessary to have a security revamped efficient firewall.
Improvement of firewall efficiency is essential[13] [18]. Having a complicated solution to read the firewall rules increase and decrease the efficiency of the firewall. Since IoT devices are equipped with limited computational resources, it is vital to have an efficient solution to read the firewall rules. [13] [18] suggests 2-dimensional classification has a higher time complexity, and it offers bit-level parallelism to reduce the time of rule access time.
Network outages are a challenge because they are frequent, hard to fix, expensive, and poorly understood by users [14] [19]. Though there are various issues surrounding network availability, the study proposed eliminating or minimizing the effects of problems caused by software attacks through networks, including worms and remote attacks to exploit server vulnerabilities. Software upgrades avoid compromising target systems through, e.g., malware and vulnerability exploits[14] [19]. Therefore, there is a limited number of patches or software upgrades are available for IoT devices. It is valuable to have a proactive defense mechanism capable of mitigating risks associated with unpatched components within an otherwise trusted TCP/IP network [14] [19].
Privacy and security issues in IoT devices are addressed at different levels from different perspectives. According to the survey AWS IoT, Kane stated [15] [20] does not depend on the programing language or the hardware or the Operating system running on them. Also, Aws has multi-layer security for IoT devices which supports mutual authentication at every point of the connection. So, the data is transmitted through the device is always known. X.509 certificates are most used for authentication purposes. It is suggested [16] [21] that Data and I/O devise usage is getting high that required artificial intelligence to eliminate the redundant data and reduce power usage through the application.
When it comes to IoT devices, it carries sensitive data and transforms these collected data into the other devices in the network. Therefore, authentication of the connected devices is essential. And the privacy of the data shared between these devices should be considered due to the lack of an encryption mechanism that carries IoT devices. According to Alotolini [17] [22], studies indicate that hardware-based firewall implementations have a latency shorter than two orders of magnitude than the software-based firewall implementations. Also, these studies suggest that software-based firewall implantation is caused in less lifetime due to the high usage of limited available resources. Therefore, it is essential to reduce the software-based firewall power consumption in IoT devices. According to the studies about “security in the internet of things,” the security required in the IoT will be higher in dependability and availability. According to Suo[18] [12], the studies show that end-to-end encryption cannot encrypt the destination address and source IP address. In order to transmit the data Source and Destination, IP addresses are required. In Addition to that, communication protocols are very rarely added to IoT devices. Due to this reason, IoT devices are more vulnerable to DDOS attacks.
There can be vulnerabilities that we cannot give patches to mitigate[19] [23]. The zero-day vulnerability is one example of that kind of attack. According to the studies, we can change the attack vector with the support of software-defined networking.
Authentication protocols prevent intruders from accessing the sensitive data in the support and application layer by adding identity identifications. These identity security mechanisms focus on authentication by certain provided services. Also, it enables users to choose the associated information to be shared with the services[20] [13]. And literary sources propound the verification of data and developing a temporary cache against malicious operations.
Since IoT devices are connected through untrusted internet networks, an Intrusion detection system is mandatory to avoid internal wireless attacks. According to Raza[21] [24], studies show that currently, available intrusion detection systems are not supporting IoT devices. This Model has end-to-end packet loss adaptation, and it can alternate the path if the destination does not receive the packet.
3 Proposed Methodology and proposed design to your mobile application.
3.1 The plan
Protecting IoT devices and services from unauthorized access both internally and externally is a part of ensuring security. Security should safeguard services, hardware resources, information, and data while they are in transit and storage.
After identifying the three main issues with IoT devices and services related to the security: data confidentiality, privacy and trust, next step is to find a solution through ubiquitous computing to safeguard IoT devices.
Protecting IoT devices and services from unauthorized access both internally and externally is a part of ensuring security. Security should safeguard services, hardware resources, information, and data while they are in transit and storage.
After identifying the three main issues with IoT devices and services related to security: data confidentiality, privacy and trust, the next step is to find a solution through ubiquitous computing to safeguard IoT devices.
To create the suggested solution, we must first identify the security issues associated with IoT devices connected to the home network. The next procedure is to recognize, manage, and control issues with IoT devices linked to the home network. After these vulnerabilities have been recognized, the proposed solution can integrate appropriate security steps to secure the home network. A computer with a considerably powerful processor and a RAM is required to build this proposed technique. The proposed computer should be required with i5 Processors, 8 GB of RAM, and 500GB of HD capacity. The proposed system is implemented in the C and C# programming languages. MSSQL is used for database purposes. Inbuilt Wi-Fi, Bluetooth, and Ethernet cables are used to interconnect Smart Home IoT devices to the proposed system.
Define requirements.
As the initiative step define the requirements of the application. Identify what functionalities needed to have in the application such as the ability to detect and connect to IoT devices, monitor their status, set up automated tasks, and receive alerts.
Device detection
The application should be able to automatically detect all IoT devices connected to the home network and provide their basic information such as device name, IP address, and MAC address.
Monitoring
The application should enable users to monitor the status of their IoT devices, including their online/offline status, power consumption, and other relevant metrics.
Control
The application should provide users with the ability to control their IoT devices, such as turning them on or off, adjusting their settings, and executing other functions.
Customization
Users should be able to customize the program to their own requirements, such as setting up alerts, establishing custom dashboards, and configuring automatic processes.
Security
The application should be secure and reliable, protecting the user’s home network from external dangers.
User management
The application should allow multiple users to access and manage the home network’s IoT devices, with different levels of permissions and access.
Integration
The app should be able to integrate to other smart home systems or platforms like Alexa, Google Home, or Apple HomeKit.
Design the user interface.
Once the requirements have been defined, begin designing the user interface. Create wireframes and mockups of the application’s screens and navigation to make sure the user interface is intuitive and easy to use.
Select development platform.
For this application, the backend will be written in C# and C, while the frontend will be a desktop application. You will also utilize MS SQL as a database to store IoT device data.
Backend development
For the application’s backend development, you will utilize C and C#. C is a low-level programming language that may be used to write code that interacts with hardware or controls system resources. C# is a high-level programming language that’s utilized to develop Windows desktop applications. C# may be used to create the core application logic, user interfaces, and interactions with the MS SQL database.
Frontend development
Desktop applications can be used to front-end development. Desktop applications run natively on the user’s computer, which delivers a faster and more responsive user experience compared to web-based applications. U se C# to create the desktop application’s user interface. The user interface should enable the user to monitor and manage the IoT devices that are connected to their home network.
Database development
Use MS SQL can be used to develop the application’s database. Microsoft SQL is a relational database management system (RDBMS) that provides a robust and secure method of storing and retrieving data. MS SQL may be used to store data on IoT devices connected to your home network, such as their device name, IP address, MAC address, and firmware version. MS SQL may also be used to store information about user accounts and their permissions.
Testing and deployment
To test the application, use testing frameworks such as NUnit or xUnit for C# and CUnit or Unity for C. To deploy the application, developers can create an installer package using tools such as InstallShield or Wix Toolset. Also consider testing the application on different operating systems and hardware configurations to ensure compatibility.
Create the backend.
Begin by creating the backend code using C and C#. Develop a program that scans the home network for IoT devices and extracts their information, such as device name, IP address, MAC address, and firmware version. Store this information in the MS SQL database.
Network scanning
The first stage in developing the backend is to scan for IoT devices on the home network. To capture network traffic and extract information about IoT devices connected to the network, use a network scanner library such as SharpPcap or Npcap. also use a protocol like UPnP to automatically find IoT devices on the network.
Data storage
Once the IoT device information has been extracted, it must be stored in the MS SQL database. ADO.NET may be used to interact with the MS SQL database from C# or C programs. Create a database schema with tables for storing device information, user accounts, and access permissions.
Authentication and authorization
Implement authentication and authorization techniques to ensure the application’s security. The Windows authentication system can be employed to authenticate users and provide them with access to the application’s functionality based on their assigned permissions.
APIs
With C#, you may develop APIs that allow the application’s frontend to interact with the backend. APIs should include ways for retrieving device information, automating actions, and receiving alarms. RESTful APIs can be utilized to provide a simple and standardized way for the frontend to interact with the backend.
Real-time updates
Developers can utilize WebSocket or SignalR to send real-time changes to the frontend. WebSocket provide bidirectional communication between the frontend and backend, but SignalR offers a higher-level abstraction for real-time communication.
Testing
Unit testing frameworks such as NUnit or xUnit can be employed to test the backend. • Unit tests should cover all backend functionality, such as device detection, data storage, authentication and authorization, and API endpoints.
Create the front end.
After constructing the backend, use the desktop application to develop the frontend. Use C# to create the user interface and connect it to the MS SQL database to retrieve and display the IoT device information.
User Interface Design
Designing the user interface is the initial stage in constructing the frontend. The user interface should be intuitive, simple to use and allow access to all of the application’s functionalities. to generate wireframes and mockups of the user interface, utilize a UI design tool such as Adobe XD or Figma.
Windows Forms or WPF
can use Windows Forms or Windows Presentation Foundation to design the user interface (WPF). Windows Forms is a simple and lightweight UI framework for creating basic desktop programs, whereas WPF is a more advanced UI framework for creating rich and dynamic user interfaces. WPF provides support for data binding, styling, and animation, making it a good choice for creating modern and visually appealing user interfaces.
UI controls and widgets
To construct the user interface, can utilize a range of UI controls and widgets such as labels, textboxes, buttons, and dropdown lists. To add more powerful UI features like charts and graphs, can utilize third-party UI frameworks such as DevExpress or Telerik.
Data binding
To show data from the backend in the user interface, can utilize data binding. Data binding creates a connection between the data in the backend and the user interface elements, allowing changes to the data in the backend to be automatically reflected in the user interface.
Event handling
can use event handling to manage user input and trigger actions in the backend. Event handling allows you to respond to user events such as button clicks and mouse movements, and trigger actions in the backend such as setting up automatic tasks or receiving notifications.
Testing
can use UI testing frameworks like WinAppDriver or CodedUI to test the frontend. UI tests should include all front-end functionality, such as user input, data binding, and event handling.
Add functionality.
Add the functionalities defined in step 1, such as monitoring device status, setting up automated tasks, and receiving notifications.
Device control
When implementing device control features, it is essential to ensure that only authorized users may control the devices. can use role-based access control (RBAC) to restrict device access to devices based on user roles and permissions. you should consider adding encryption to protect user credentials and device control commands from interception or tampering.
Automatic tasks
If not properly configured, automated tasks might introduce security vulnerabilities. You should ensure that automated tasks are only initiated by authorized users and do not have any unintended consequences, such as turning off crucial devices. ou can implement a review and approval process for new automated tasks, to ensure that they are safe and effective.
Alerts and notifications
While alerts and notifications can be useful in informing users about device condition and performance, they can also be exploited to transmit phishing attacks or malware. You should make certain that notifications are only issued from trustworthy sources, and that users are trained to detect and avoid phishing frauds.
User management
Because unauthorized access to the application or the home network can lead to data theft, device compromise, or other harmful behaviors, user management is a crucial part of security. To safeguard user accounts, deploy strong authentication mechanisms such as multi-factor authentication (MFA) to protect user accounts. . You should also keep an eye on user activity for signals of strange or suspicious behavior.
Integration with other systems
Integration with other smart home systems or platforms can introduce security risks if not properly configured. You should make certain that only authorized devices and services can access the application, and that they use secure communication protocols such as TLS. You should also monitor the logs of the application and the integrated systems for signs of unusual or malicious activity.
Reporting and analytics
Reporting and analytics may give significant insights into device performance and user behavior, but if not adequately protected, they can potentially expose sensitive information. Individual restrictions and encryption should be implemented to secure sensitive data, and only authorized individuals should have access to reports and analytics.
Test the application.
Once the software has been developed, extensively test it to confirm that it functions as expected. To ensure compatibility, test the application with several types of IoT devices.
Lastly, deploy the program to the target machines and configure it to execute automatically when the system boots. Ensure that the program can operate in the background without interfering with system performance.
Maintaining the program entails fixing bugs, releasing updates, and gradually improving its functionality.
A computer with a powerful processor with i9 Processors, 8 GB of RAM, and 500GB of HD capacity can be used to secure a smart home by running security applications that monitor and defend the interconnected smart devices and network.
To ensure the security of a smart home, the computer must have a powerful processor with multiple cores to manage the demands of running security software and applications. Intel Core i7 or i9 processors or AMD Ryzen 7 or 9 processors would be appropriate for this purpose. Additionally, the computer should have at least 8GB of RAM to ensure smooth and efficient multitasking.
Antivirus software, firewalls, and intrusion detection/prevention systems are examples of security software and applications that can be operated on a computer. These programs can scan and eliminate malware, protect against unauthorized access, and alert the user of any suspicious activity on the network.
In addition to security software, the computer can be used to monitor and control smart devices in the home. For example, it can be used to configure network settings, set up access controls, and manage user accounts.
Overall, a computer with a powerful processor sufficient RAM can be utilized to secure a smart home by running security applications that monitor and defend the interconnected smart devices and network. It is crucial to highlight, however, that securing a smart home requires a comprehensive approach that involves not only the computer, but also the smart devices, the network, and the user’s behavior.
For database purposes, Microsoft SQL Server (MSSQL) can be a better solution for securing a smart home. MSSQL is a relational database management system designed to handle massive volumes of data while maintaining high performance and strong security features. These are some examples of how MSSQL can be used to secure a smart home.
MSSQL can be used to store information about smart home devices such as their type, status, location, and access control settings. This information can be used to monitor devices and enforce security regulations.
MSSQL can be used to store user credentials and access control policies for user authentication and authorization. This can be used to authenticate users and authorize them permission to access smart home devices and data.
MSSQL can be used to store records of network activity, device events, and user actions for logging and auditing. This is useful for tracking security incidents, detecting anomalies, and investigating security breaches.
Backup and recovery: MSSQL include backup and recovery features that can be used to safeguard smart home information in the case of a data loss or system failure.
MSSQL provides strong encryption and access control features that can be used to secure smart home data from unauthorized access or data theft. Transparent data encryption, cell-level encryption, and role-based access control are all part of this.
Overall, adopting MSSQL for database purposes can deliver a reliable, scalable, and secure solution for security systems for smart homes. However, it is important to properly configure and maintain the MSSQL server to ensure that it operates securely and efficiently. Applying security patches, configuring backup and recovery settings, and monitoring database activity for security issues are all part of this.
Depending on the specific requirements and security goals, using C and C# programming languages to secure a smart home can involve several approaches The C and C# programming languages can be used to protect a smart home in the following ways:
C and C# can be used to construct network monitoring tools that analyze network traffic and detect anomalous patterns. This can aid in the detection of network intrusions, malware infections, and other potential threats.
Access control C and C# can be used to create access control mechanisms that limit users’ and devices’ access to the smart home network and devices. These can include systems for authentication and authorization systems, password policies, and encryption.
Device management the programming languages C and C# can be used to develop device management tools that monitor the state and behavior of smart home devices. Firmware upgrades, configuration management, and error reporting are all examples of this.
Alerting and response the programming languages C and C# can be used to develop alerting and response mechanisms that can warn users and security personnel of security incidents and automate incident response processes. Email notifications, SMS alerts, and automated actions according to predefined rules are examples of this.
Machine learning and artificial intelligence (AI) C and C# can be used to develop machine learning and AI algorithms capable of analyzing smart home data and detecting trends that indicate security issues. Anomaly identification, predictive modeling, and behavioral analysis are all examples of this.
Ultimately, securing a smart home with C and C# programming languages to secure a smart home necessitates a comprehensive approach that includes multiple security measures as well as constant monitoring and response. It is important to consider the specific requirements and security goals of the smart home and choose the appropriate tools and techniques to achieve those goals.
Wi-Fi, Bluetooth, and Ethernet cables included into smart home IoT devices can be used to interconnect smart home IoT devices and assist secure a smart home network in a variety of ways:
Wi-Fi is a wireless networking technology that enables devices to connect to networks without the use of cables. It’s prevalent in smart home products like smart thermostats, security cameras, and smart speakers. Wi-Fi networks can be secured against unauthorized access and data theft by utilizing encryption protocols such as WPA2 or WPA3. It is important to ensure that Wi-Fi networks are properly configured, use strong passwords, and have firmware updates applied to ensure that they remain secure.
Bluetooth is a short-range wireless technology that is often utilized in smart home devices like smart locks and light bulbs. Bluetooth devices have a narrower range than Wi-Fi devices, which can assist in minimizing the danger of unauthorized access. Bluetooth networks can also be protected with encryption protocols such as Bluetooth Low Energy (BLE) Security, which protects against unauthorized access and data theft.
Ethernet cables are used to connect smart home devices directly to a router or switch, ensuring a reliable and secure connection. Ethernet networks can be protected against unauthorized access and data theft by utilizing encryption protocols such as Transport Layer Security (TLS). It is critical to ensure that Ethernet networks are correctly configured and physically secured in order to prevent unauthorized network access.
In addition to these technologies, other security measures, such as implementing a firewall, configuring VLANs to segregate different devices, and regularly updating firmware and software to ensure that they are up to date and patched against known vulnerabilities, can be implemented to help secure a smart home network.
3.2 methodology of carrying out the project interviews(questionnaires)
Schedule time with target audience and conduct the interviews either in person or remotely using video conferencing tools.
3.2.1 DESCRIPTIVE QUESTIONS –
What are some common security threats that IoT devices face in a home environment?
Answer: Common security threats for IoT devices in a home environment include malware infections, botnet attacks, phishing attacks, and data theft. These threats can be particularly dangerous because IoT devices often have weak security and are constantly connected to the internet.
What steps can homeowners take to protect their IoT devices from cyberattacks?
Answer: Homeowners can take several steps to protect their IoT devices, such as using strong and unique passwords for each device, updating device firmware and software regularly, isolating IoT devices on a separate network, using firewalls, and avoiding public Wi-Fi networks when possible.
What are some features that you would like to see in a firewall application for IoT devices in a home environment?
Answer: Some features that I would like to see in a firewall application for IoT devices in a home environment include a user-friendly interface, the ability to customize firewall rules for individual devices, real-time threat detection and blocking, and automatic firmware and software updates.
How important is ease of use when it comes to setting up and configuring a firewall for IoT devices in a home environment?
Answer: Ease of use is extremely important when it comes to setting up and configuring a firewall for IoT devices in a home environment, as many homeowners may not have technical expertise in network security. A user-friendly interface and clear instructions can make the setup process much easier and reduce the risk of misconfiguration.
How much technical knowledge do you think is necessary to set up and maintain a firewall for IoT devices in a home environment?
Answer: Some technical knowledge is necessary to set up and maintain a firewall for IoT devices in a home environment, but the level of expertise required will depend on the complexity of the firewall application and the devices being protected. However, with the right instructions and user interface, even users with minimal technical knowledge should be able to set up and maintain a basic firewall for their IoT devices.
What are some challenges that homeowners might face when setting up a firewall for their IoT devices?
Answer: Some challenges that homeowners might face when setting up a firewall for their IoT devices include compatibility issues with different devices, the need for technical expertise, conflicting settings between different devices and applications, and the need to balance security with ease of use.
What type of user interface do you think would be most effective for a firewall application for IoT devices in a home environment?
Answer: I think a user interface that is intuitive and easy to use, with clear instructions and explanations, would be most effective for a firewall application for IoT devices in a home environment. A dashboard that provides a clear overview of all connected devices and their security status would also be helpful.
How would you prioritize different firewall rules and settings when setting up a firewall for IoT devices in a home environment?
Answer: When setting up a firewall for IoT devices in a home environment, I would prioritize rules and settings that provide the greatest level of security without compromising the functionality of the devices. This might include blocking incoming traffic from unknown sources, isolating IoT devices on a separate network, and setting up rules to block known malicious traffic.
What are some best practices for setting up and configuring a firewall for IoT devices in a home environment?
Answer: Some best practices for setting up and configuring a firewall for IoT devices in a home environment include updating device firmware and software regularly, using strong and unique passwords, isolating IoT devices on a separate network, using firewalls, and avoiding public Wi-Fi networks when possible.
How do you think the role of firewalls for IoT devices will evolve in the future?
Answer: I think the role of firewalls for IoT devices will become increasingly
3.2.2 MULTIPLE CHOICE QUESTIONS –
How familiar are you with the concept of a smart home and its related technologies?
Yes No
Have you ever used any smart home devices (e.g., smart thermostat, smart light bulb, smart lock, etc.)? If so, which ones?
Yes No
What kind of information do you think is sensitive and needs to be secured in a smart home environment?
Personal information Financial Information Security system information
Health Information User behavior information Device information
What security measures do you think should be implemented to protect information in a smart home environment?
| Secure network | Limit access | ||
| Firewall | Disable unused features | ||
| Two-factor authentication | Disable unused features | ||
| Regular updates | Physical security | ||
| Strong passwords |
Have you ever experienced any security breaches or attacks in your smart home environment? If so, how were they resolved?
Yes No
What features would you like to see in a mobile application that can manage and control your smart home devices?
| User-friendly interface | Analytics | ||
| Compatibility | Security | ||
| Voice control | Notifications | ||
| Automation | Energy efficiency | ||
| Remote access | Integration |
How important is it for you to have a unified interface that can manage and control all your smart home devices from a single mobile application?
high Moderate Low
Do you have any concerns about using a mobile application to control your smart home devices? If so, what are they?
Yes No
How comfortable are you with the idea of your smart home devices collecting data about your activities and behaviors?
High Moderate Low
What kind of data would you be comfortable sharing with smart home devices, and what kind of data would you prefer to keep private?
| Data to share with smart homes | Data to keep private | ||
| Device usage data | Financial information | ||
| Environmental data | Health information | ||
| Personal information | Location data | ||
| Behavioral data | Personal communication | ||
| Voice and audio data |
3.3 questionnaires/secondary data (referring Internet Resources)
Research studies or reports on the security risks and challenges associated with IoT devices in a home environment. For example, the report “Securing Your Connected Home” by the National Cyber Security Alliance and the Department of Homeland Security provides an overview of common security risks and recommendations for protecting IoT devices in a home environment.
Technical documentation or manuals for different firewall software or hardware. For example, the documentation for the popular open-source firewall application, pfSense, provides detailed instructions on how to set up and configure a firewall for IoT devices.
Reviews and feedback from users of existing firewall applications for IoT devices. For example, online forums and review sites such as Reddit and CNET may provide insights into the effectiveness and usability of different firewall applications.
Articles or blog posts by cybersecurity experts on best practices for securing IoT devices in a home environment. For example, the article “5 Ways to Secure Your IoT Devices” by Tom’s Guide provides practical tips for securing IoT devices in a home environment.
Industry publications or news articles on emerging trends and technologies related to IoT security. For example, the article “IoT Security: A Comprehensive Guide” by Security Intelligence provides an overview of emerging trends and technologies related to IoT security.
Online forums or discussion boards where homeowners or IT professionals discuss their experiences setting up and maintaining a firewall for IoT devices. For example, the Home Networking subreddit may provide insights into the challenges and best practices for setting up a firewall for IoT devices in a home environment.
Data on the frequency and types of cyberattacks targeting IoT devices in a home environment. For example, the Internet of Things Cybersecurity Improvement Act of 2020 requires the National Institute of Standards and Technology to create guidelines for securing IoT devices and to track cybersecurity threats to IoT devices. This data may provide insights into the most common types of cyberattacks targeting IoT devices in a home environment.
3.4 interface design to get information anywhere and any place.
3.4.1 LOGIN SCREEN
After login to screen homeowners navigate to main screen which shows all the devices connected to the network
In here homeowners can have three logins for most trustworthy family members.
3.4.2 MAIN SCREEN
- We can see connected devices to the network.
- We can see device information.
- After clicking on a device, we can navigate to each device.
In here homeowners can monitor the connected devices and their connection, alerts or the notifications are appeared in notification panel, after clicking each of these devices’ owners can obtain a specific report for each of the device connected.
3.4.3 DEFAULT DEVICE SCREEN
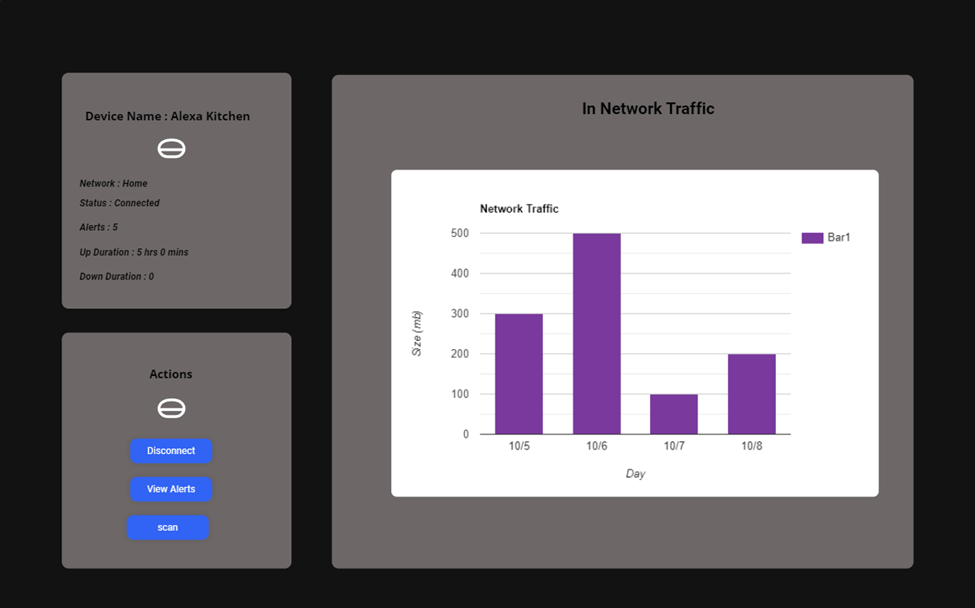
- We can see data flows into the application.
- We can scan a device for issues.
- We can see alerts.
Data flows means is there any kind of vulnerability or risk it will indicate in this panel. Also, the network traffic which is caused due to the interconnections of several number of IoT devices can be seen here.
In traffic of the devices can be monitors by this interphase
If the owners want to disconnect any device to ensure security, it can also be completed through this panel.
3.4.4 Out Traffic Interface
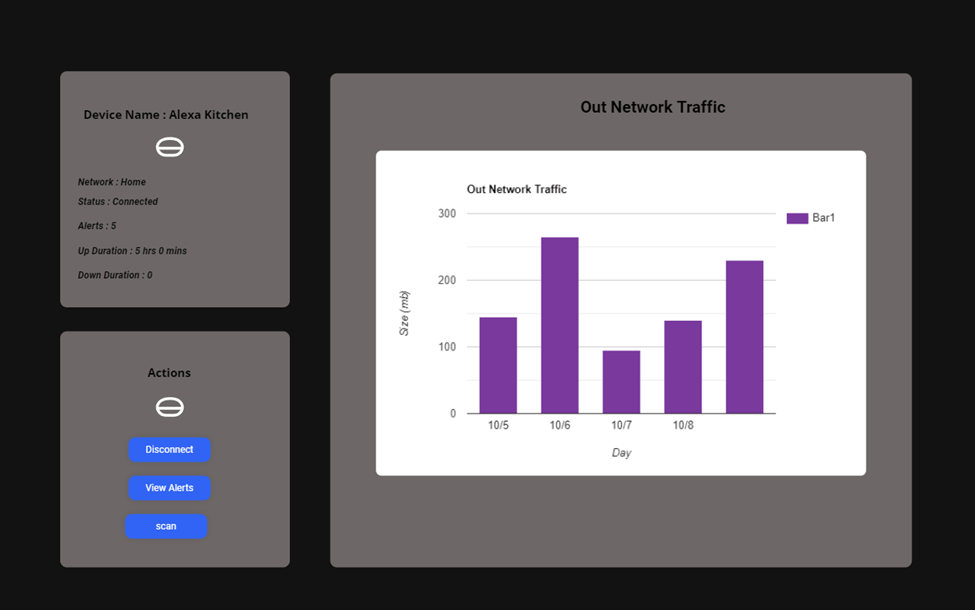
- We can see traffic going out of the device.
Out traffic or the traffic flows of several interconnected IoT devices can be monitor from this panel.
3.4.5 ALERTS INTERFACE

- Received alerts for screen.
- We can take action on each alert.
This is the most significant panel which is the alerts history. Any actions taken by the owners or users of any disconnected devices can be seen here with date and time.
3.4.6 SCAN INTERFACE
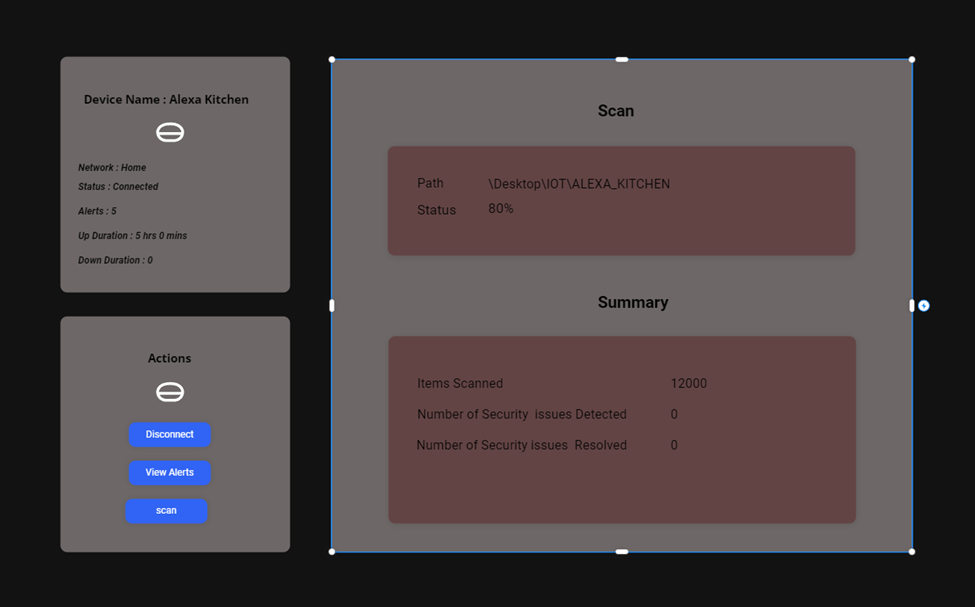
- Device scan information
- Device scan progress
Scanning is the most essential requirement in a smart home, daily scanning can assist in minimizing the risk of threats and vulnerabilities. Scanning information is indicated in this panel. Also is there any updates required for the IoT devices, that will also notified in this panel.
4 Discussion of the proposed Mobile Ubiquitous Computing solution
By enabling remote management and control of IoT devices via mobile ubiquitous devices, mobile ubiquitous computing solutions can significantly improve the convenience and security of smart homes. This piece of report discovers a Mobile Ubiquitous Computing Solution to Secure, Manage and Control information of Internet of Things (IoT) in a smart home, Following is the discussion on some examples of mobile ubiquitous computing systems that are used in modern smart homes and their technologies which used to enhance the efficiency and effectiveness of the smart homes and their security.
| Analysis on technologies used in smart homes | How the technology is used in proposed solution |
| MOBILE APPLICATIONS In a smart home, mobile applications can be utilized to remotely manage and control IoT devices. Users can use their smartphone or tablet to operate devices such as lights, thermostats, and security cameras through the mobile application. | This is the basic technology used in this centralized unit where users can access each and every smart device in the home by one touch through a tablet or a mobile phone and users can observe the risk and vulnerabilities towards the smart home devices |
| LOCATION-BASED SERVICES When a user enters or exits a specific location, location-based services can be utilized to automatically trigger actions in a smart home. For example, when the user enters the house, the smart home can switch on the lights and turn them off when the user exits. | All the smart devices can be monitored through centralized unit and if unauthorized person enters the house that can be detected through the control panel since the instances which activate the smart devices are recorded. |
| VOICE ASSISTANTS Amazon Alexa and Google Assistant, for example, can be interconnected with smart home devices to enable voice control. Voice commands can be used to turn on/off lights, regulate thermostats, and conduct other operations. | Voice assistants can be interconnected with the centralized device and the data flow will indicate if an unauthorized person is trying to access the voice assistance. Unusual usage of device also can be notified |
| WEARABLE GADGETS Smartwatches and other wearable devices can be used to remotely manage and control smart home devices. Users can use their wearable gadget to access the mobile application and control devices without having to take out their smartphone. | Wearable gadgets playing a major role in this specific device since the unit is granting permission to access the smart home devices for authorized people only. Also system denies the access weak and vulnerable devices. |
| INTELLIGENT AGENTS In a smart home, intelligent agents can be employed to automate routine operations. When a user leaves the house, an intelligent agent can be programmed to turn off all lights and lock all doors. | The centralized unit is Operated as an intelligent agent. When the homeowners are outside from the house and the house is at a risk or vulnerable to a threat the unit can inform it through alerts and the security precautions Like locking Doors, disconnecting devices can be implemented through the device. |
| SECURE AUTHENTICATION Before granting access to Internet of things included in a smart home , mobile applications can be utilized to securely authenticate users. This can be accomplished by biometric identification, such as fingerprint or facial recognition, or through using a secure password. | In the initiating step of the implementation of this unit, the data of authorized users are entered to the unit. Then the unit can identify the authorized people through specific fingerprint, facial, voice, eye recognitions. Also, the wearable devices of authorized users authenticate by syncing data. Also proposed solution can identify unusual login behavior through history of login and send notifications or take appropriate actions. |
| SECURE COMMUNICATION PROTOCOLS Most IoT Systems use http protocol due to low computing power of IoT. Mostly VPNs are not used. | Since this centralized unit is developed to ensure the security, the technology is consisted with VPN, HTTPS secured communication protocols which ensure that data transmitted between devices is encrypted and that intruders cannot intercept it. |
| REMOTE MONITORING Mobile ubiquitous applications can be utilized to remotely monitor IoT devices in a smart home, delivering real-time warnings and notifications in the event of any suspicious activity or security breach. | As previously mentioned, the most significant feature of this centralized unit is that the homeowners can monitor and secure the home using Secure communication mediums. |
| DEVICE MANAGEMENT In a smart home, mobile ubiquitous applications can be used to manage and control IoT devices, such as setting up new devices, adjusting settings, and updating firmware. | Through this centralized unit, users can update their all devices. If the users want to include devices to the smart home that also accomplished through this unit. Also it can scan for newly available vulnerabilities and patch them. |
| DATA ENCRYPTION Mobile ubiquitous applications can be utilized to encrypt data transmitted between IoT devices and the mobile device, ensuring that sensitive information is protected from unauthorized access. | As mentioned previously, secure communication protocols will lead to ensure that sensitive information is protected from unauthorized access while transmitting data through data encryption. And since we are using centralized system, we can include strong Encryption mechanisms with higher computing capacity |
| FIREWALL PROTECTION Firewall protection for IoT devices in a smart home can be implemented using mobile ubiquitous applications, preventing unauthorized network access, and blocking dangerous data. | Firewalls should be update and can be implemented through this centralized unit. Having a dedicated firewall for this set of IoT devices increase the security of the environment. |
| AUTOMATIC BACKUPS In the instance of a security breach or device failure, mobile ubiquitous applications can be used to automatically backup IoT device settings and data, ensuring that they can be readily restored. | Since the ensuring security is the most important factor in this centralized unit, backup process of IoT device settings and data automatically carried out by the system. |
In conclusion, mobile ubiquitous computing solutions can deliver an integrated and secure platform for managing and controlling IoT devices in a smart home. By implementing these solutions, users can take advantage of a connected and convenient smart home simultaneously ensuring the privacy and security of their personal information. Mobile ubiquitous computing solutions can greatly enhance the convenience and security of smart homes by enabling remote management and control of IoT devices through mobile devices.
5 Conclusions and recommendations.
5.1 Recommendations
Recommendations to develop the Mobile Ubiquitous Computing Solution to Secure, Manage and Control information of Internet of Things (IoT) used in smart home.
As more individuals adopt Internet of Things (IoT) technologies such as smart thermostats, security cameras, and lighting systems, smart homes are becoming more popular. Nevertheless, because these gadgets are frequently connected to the internet, they can be vulnerable to hacking and data breaches and lead to security risks. Mobile Ubiquitous Computing Solutions (MUCS) can provide a secure, efficient, and effective means of managing and controlling the information generated by smart home devices. And it is vital to be updated about the new technologies specially related to mobile ubiquitous computing solutions which can be used to Secure, Manage and Control information of Internet of Things (IoT) used in smart home.
Mobile device management (MDM) and enterprise mobility management (EMM) solutions are one way that Mobile ubiquitous computing solutions can safeguard smart home devices. These solutions can be used to ensure that smart home devices are correctly configured and secured, as well as to manage data flow between smart home devices and mobile devices. To prevent unauthorized access to sensitive data, MDM and EMM can also be used to impose security policies such as password restrictions and remote device wiping.
Mobile Device Management (MDM) MDM software is capable of managing and securing mobile devices used to access and control smart homes. MDM software has the ability to control device access, enforce security regulations, and remotely wipe data from lost or stolen devices.
Another important technology that may be used to secure smart home devices is Identity and Access Management (IAM). IAM solutions can be utilized to manage user identities, access to smart home devices, and the information generated by them. Organizations can use IAM to ensure that only authorized users have access to smart home devices and the data generated by them.
Virtual private networks (VPNs) and data encryption are two more significant technologies that are capable of securing smart home devices. VPNs can be used to securely interconnect mobile devices to smart home devices, ensuring the prevention of unauthorized access to data. Data encryption can be used to protect data generated by smart home equipment by transforming it into a code that only a secret key can decipher.
In addition to security, Mobile ubiquitous computing solutions can also help to monitor and control smart home devices. Mobile ubiquitous computing solutions systems, for example, can be used to monitor the status of smart home devices as well as perform remote diagnostics and troubleshooting. This can help to decrease downtime while also improving the overall reliability and performance of smart home devices.
NFC (Near Field Communication)NFC is a short-range wireless communication technology OR PROTOCOL that can be utilized to transmit data BY integrating and controlling smart home devices. NFC tags could be placed on various objects or in different rooms in a smart home context to trigger specific actions or settings. Secure pairing methods and encryption techniques can be used to secure NFC devices.
Augmented Reality (AR) Technology this technology can be utilized to provide users with additional information or guidance while interacting with smart home devices. Users may, for example, utilize AR to see information about their appliances’ energy usage or to obtain visual clues while adjusting settings.
Mobile payments Mobile payment technologies such as Apple Pay and Google Pay can be integrated with smart home devices to enable transactions such as online shopping and home service purchases and payments.
Bluetooth is a wireless communication protocol used for connecting and controlling smart home devices. Bluetooth devices can be secured by employing secure pairing and encryption mechanisms.
Zigbee is a low-power wireless communication protocol popular in smart home devices. Encryption techniques and access control mechanisms can be used to safeguard Zigbee devices.
RFID (Radio Frequency Identification)RFID is a wireless communication protocol that can connect and control smart home gadgets. RFID devices can be secured by employing access control mechanisms and encryption methods.
Wi-Fi is a wireless communication protocol widely utilized in smart home devices. Encryption techniques and access control mechanisms can be used to secure Wi-Fi devices.
VPNs can be used to establish a secure and private connection between a mobile device and a smart home device. This ensures that data transmitted between two devices is encrypted and secure.
Authentication and authorization Before granting access to sensitive information or permitting device operation, smart home devices can be configured to require user authentication. Passwords, fingerprints, and multi-factor authentication can be used to achieve that.
Biometric Authentication Mobile devices can utilize biometric authentication methods such as fingerprint recognition, facial recognition, or voice recognition to ensure that only authorized users can access the smart home devices.
Encryption Data transmitted between two smart home devices and mobile devices can be encrypted with secure protocols like HTTPS, SSL, or TLS. This ensures that the information is protected from unauthorized access or interception.
Access control Access control techniques can be implemented to restrict access to sensitive areas of the smart home to authorized personnel only. This can be accomplished through the use of techniques such as role-based access control and attribute-based access control.
Remote monitoring and management Homeowners can use mobile apps to remotely monitor and manage their smart home devices. Remote device control, real-time alerts, and data analytics are all included.
Secure Remote Access Users may operate and monitor their homes from anywhere by using mobile devices to enable secure remote access to smart home equipment. This feature can be secured with methods of encryption and authentication.
Cloud-based services Smart home data can be stored and processed through cloud-based services. This allows for secure and scalable storage, as well as data analysis capabilities.
Secure Cloud-based Storage Smart home information is securely stored in the cloud-based storage. To prevent data loss or theft, this data can be encrypted and backed up.
Security Based on Machine Learning and AI Machine learning and AI can be used to monitor and analyze behavioral trends and activity within the smart home to identify potential security threats or abnormalities.
AI-based Security AI-based security systems could monitor and analyze behavior trends and activity within the smart home to detect potential security risks or anomalies. This can aid in the prevention of unauthorized access and attacks.
Firewalls and Intrusion Detection Systems (IDS) Firewalls and IDS can be used to protect smart homes from unauthorized access and attacks. These systems are capable of detecting and blocking malicious traffic from entering the smart home network.
5.2 RECOMMENDATIONS TO SMART HOMEOWNERS
Smart home security is critical since these houses are increasingly connected to the internet and vulnerable to cyber threats. Here are some measures that can be made to improve smart home security:
A secure Wi-Fi network with a strong and unique password smart home device should be connected to a secure Wi-Fi network with a strong and unique password. WPA2 encryption should be used on the Wi-Fi network, and the SSID (Service Set Identifier) should be hidden.
Frequent software updates to ensure that any vulnerabilities or security vulnerabilities are fixed, smart home devices should be regularly updated with the latest software and firmware updates.
Strong passwords Users should use strong and unique passwords for their smart home devices and should avoid using default passwords or easy-to-guess passwords.
Two-factor authentication owners should enable two-factor authentication on their smart home devices, which adds an extra layer of security by requiring a second form of verification, such as a fingerprint or one-time password.
Restrict access Users should restrict access to their smart home devices by granting access only to trustworthy personnel and utilizing access controls such as user accounts and permissions.
Monitor network traffic owners should be monitoring the network traffic of their smart home devices to detect any unusual activity or traffic.
Use firewalls to secure smart home devices from unauthorized access and malicious traffic, users should utilize firewalls.
Disable unnecessary features to reduce the attack surface and the risk of security breaches, users should disable any unnecessary functions on their smart home devices.
Users should exercise caution when downloading and installing third-party apps for their smart home devices, as these apps ma`y include malware or other security vulnerabilities.
Users can enhance the security of their smart homes and reduce the risk of cyber-attacks and security breaches by adopting these actions.
6 CONCLUSION
Finally, Mobile Ubiquitous Computing Solutions (MUCS) can provide a comprehensive solution for securing, managing, and controlling data and information generated by smart home devices. Organizations may ensure that smart home devices are properly configured, secured, and maintained, and that only authorized users have access to sensitive data utilizing technologies such as mobile device management, identity and access management, virtual private networks, and data encryption etc.
Ultimately, these Mobile Ubiquitous computing technologies have the potential to be leveraged to create a secure and managed smart home environment controlled by mobile devices. To ensure that the smart home environment is secure and protected from potential threats, it is critical to create a comprehensive security strategy that encompasses all aspects of it.
Mobile ubiquitous computing solutions can be an efficient approach to secure, manage, and control information in an IoT system for the smart home. With the development of IoT devices, there is a rising need for robust security measures to secure personal information and maintain control over devices.
Mobile ubiquitous computing solutions can provide an effective means of managing these devices from a single interface, allowing users to control access, set permissions, and monitor usage. This aids in preventing unauthorized access, reducing the risk of data breaches, and improving overall security.
Moreover, mobile ubiquitous computing solutions can aid in the automation of numerous operations in the smart home, resulting in increased efficiency and convenience. Smart homes can provide a seamless experience that enhances user comfort and convenience by integrating multiple devices and sensors.
However, great attention must be made to system design and implementation in order to fully utilize the benefits of mobile ubiquitous computing solutions in a smart home IoT system. Security must be built into the system from the ground up. and devices must be meticulously integrated and tested to assure compatibility and reliable performance.
Overall, mobile ubiquitous computing solutions appear to be a promising way to secure, manage, and regulate information in a smart home IoT system, allowing homeowners to enjoy increased convenience and peace of mind.
7 References
| [1] | Rajanarthagi, “What is IoT? & Role of IoT in digital marketing,” What is the Internet of Things?, 01 december 2020. [Online]. Available:https://www.gecdesigns.com/blog/role-of-iot-in-digital-marketing[Accessed: 06-Mar-2023]. |
| [2] | S. Shea, ““What is ubiquitous computing pervasive computing (ubiquitous computing),” Internet of things networking, 30 October 2019. [Online]. Available: https://www.techtarget.com/iotagenda/definition/pervasive-computing-ubiquitouscomputing#:~:text=Pervasive%20computing%2C%20also%20called%20ubiquitous,to%20interact%20with%20computers%20as. [Accessed: 06-Mar-2023]. |
| [3] | anonymous, “Internet of Things – How it Works in Access Control,” TECHNOLOGIES. [Online]. Available:https://www.getkisi.com/guides/internet-of-things-iot |
| [4] | M. A. a. G. M. Køien, “Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks,” Journal of Cyber Security and Mobility, vol. 4, no. 1, p. 88, 22 05 2015. [Online]. Available:https://www.riverpublishers.com/journal_read_html_article.php?j=JCSM/4/1/4[Accessed: 16-Mar-2023]doi: https://doi.org/10.13052/jcsm2245-1439.414 |
| [5] | J. Sen, “Ubiquitous Computing: Applications, Challenges and Future Trends,” Embedded Systems and Wireless Technology, pp. 1–40, July 2012.[Online] Available:https://www.researchgate.net/publication/300580719_Ubiquitous_Computing_Applications_Challenges_and_Future_Trends[Accessed: 10-Mar-2023]doi: 10.1201/b12298-2 |
| [6] | C. BasuMallick, “Ubiquitous computing or pervasive computing connects every object and device around to each other and the internet., Spiceworks, ” What Is Ubiquitous Computing (Pervasive Computing)? Meaning, Layers, Examples, and Applications, 11 July 2022. [Online]. Available: https://www.spiceworks.com/tech/iot/articles/what-is-ubiquitous-computing/. [Accessed: 06-Mar-2023]. |
| [7] | A. Anand, “Ubiquitous Computing: Characteristics, Advantages & Challenges,” Information Technology, Analytics Steps, 09-Jun-2022. [Online]. Available:https://www.analyticssteps.com/blogs/ubiquitous-computing-characteristics-advantages-challenges. [Accessed: 08-Mar-2023]. |
| [8] | W. Dai, “Information Technolog: New Generations,” Data Profiling Technology of Data Governance Regarding Big Data: Review and Rethinking, p. 450, April 2016. [Online]. Available:https://link.springer.com/chapter/10.1007/978-3-319-32467-8_39 doi: 10.1007/978-3-319-32467-8_39 |
| [9] | N. Gupta, “A firewall for Internet of Things,” 08 January 2017. [Online]. Available:https://www.researchgate.net/publication/317553878_A_firewall_for_Internet_of_Things[Accessed: 15-Mar-2023]. doi: 10.1109/COMSNETS.2017.7945418 |
| [10] | D. Miorandi, S. Sicari, F. De Pellegrini, and I. Chlamtac, a, “Internet of things: Vision, applications and research challenges,” Ad Hoc Networks, vol. 10, no. 07, pp. 1497–1516 September 2012. [Online]. Available: https://www.sciencedirect.com/science/article/abs/pii/S1570870512000674 [Accessed: 06-Mar-2023]. doi: https://doi.org/10.1016/j.adhoc.2012.02.016 |
| [11] | M. A. Geir M. Køien, “Security and privacy in the Internet of Things: Current status and open issues,” in PRISMS 2014 The 2nd International Conference on Privacy and Security in Mobile Systems (PRISMS), Aalborg, Denmark, 11 May 2014.[Online]. Available:https://www.researchgate.net/publication/269687360_Security_and_privacy_in_the_Internet_of_Things_Current_status_and_open_issues[Accessed: 11-Mar-2023].doi: 10.1109/PRISMS.2014.6970594 |
| [12] | J. Wan, H. Suo, C. Zou and J. Liu, “Security in the Internet of Things: A Review,| IEEE conference …,” 2012 International Conference on Computer Science and Electronics Engineering, ” 23 April 2012.[Online]. Available: https://ieeexplore.ieee.org/document/6188257.[Accessed: 09-Mar-2023].doi: 10.1109/ICCSEE.2012.373 |
| [13] | E. Leloglu, “A Review of Security Concerns in Internet of Things,” Journal of Computer and Communications, vol. 5, no. 1, p. January, 2017. [Online]. Available:https://www.scirp.org/journal/paperinformation.aspx?paperid=73675 Accessed: 17-Mar-2023].doi: 10.4236/jcc.2017.51010 |
| [14] | K. M. A. Mohammad Rafsun Islam1*, “An Analysis of Cybersecurity Attacks against Internet of Things and Security Solutions,” Journal of Computer and Communications , vol. 08, no. 04, April 2020. [Online]. Available: https://www.scirp.org/journal/paperinformation.aspx?paperid=99316. [Accessed: 07-Mar-2023]. doi: 10.4236/jcc.2020.84002 |
| [15] | Z. CHANG, “Inside the Smart Home: IoT Device Threats and Attack Scenarios, Inside the Smart Home: IoT Device Threats and Attack Scenarios – Nouvelles de sécurité – Trend Micro FR, ” Internet of Things, Research, Vulnerabilities, Exploits, Device Management, 30 July 2019. [Online]. Available: https://www.trendmicro.com/vinfo/fr/security/news/internet-of-things/inside-the-smart-home-iot-device-threats-and-attack-scenarios[Accessed: 09-Mar-2023]. |
| [16] | K. F. A. B. Sylvain Kubler, “A standardized approach to deal with firewall and mobility policies in the IoT,” Pervasive and Mobile Computing, vol. 20, p. 114, July 2015. [Online]. Available:http://sylvainkubler.fr/wp-content/themes/biopic/images/publications/documents/PervMobComp.pdf |
| [17] | S. Acharya, J. Wang, Z. Ge, T. Znati and A. Greenberg, “Simulation study of firewalls to aid improved performance,” p. 08, May M 2006. [Online]. Available:https://www.researchgate.net/publication/4232595_Simulation_Study_of_Firewalls_to_Aid_Improved_Performance[Accessed: 09-Mar-2023].doi: :10.1109/ANSS.2006.42 |
| [18] | T. L. a. D. Stiliadis, “High-Speed Policy-based Packet Forwarding Using Efficient Multi-dimensional,” Applications, technologies, architectures, and protocols for computer communication, p. 214, 01 October 1998. [Online]. Available:https://dl.acm.org/doi/10.1145/285237.285283[Accessed: 14-Mar-2023].doi: https://doi.org/10.1145/285237.285283 |
| [19] | S. G.-M. D. R.-O. H. J. Y. J. R. M. Bruno Cruz, “A Practical Approach to Protect IoT Devices against Attacks and Compile Security Incident Datasets,” Scientific Programming, 27 April 2019. [Online]. Available:https://www.hindawi.com/journals/sp/2019/9067512/[Accessed: 14-Mar-2023].doi: https://doi.org/10.1155/2019/9067512 |
| [20] | G. R. ,. B. C. Mahmoud Ammar, “Internet of Things: A survey on the security of IoT frameworks,” Journal of Information Security and Applications, vol. 38, p. 27, February 2018.[Online]. Available:https://www.sciencedirect.com/science/article/abs/pii/S2214212617302934[Accessed: 04-Mar-2023].doi: https://doi.org/10.1016/j.jisa.2017.11.002 |
| [21] | G. T. A. J. J. Dhananjay Singh, “A survey of Internet-of-Things: Future vision, architecture, challenges and services,” 24 April 2014. [Online]. Available:https://ieeexplore.ieee.org/document/6803174 [Accessed: 04-Mar-2023].doi:10.1109/WF-IoT.2014.6803174 |
| [22] | N. B. C. T. V. L. Diego Altolini, “Low Power Link Layer Security for IoT:Implementation and Performance Analysis,” 22 August 2013. [Online]. Available:https://www.semanticscholar.org/paper/Low-power-link-layer-security-for-IoT%3A-and-analysis-Altolini-Lakkundi/753bd526875ca133afd7562864c5fc1238a5412b[Accessed: 08-Mar-2023].doi: 10.1109/IWCMC.2013.6583680 |
| [23] | B. Arrington, L. Barnett, R. Rufus and A. Esterline, “Behavioral Modeling Intrusion Detection System (BMIDS) Using Internet of Things (IoT) Behavior-Based Anomaly Detection via Immunity-Inspired Algorithms,” 15 September 2016. [Online]. Available:https://www.researchgate.net/publication/308189869_Behavioral_Modeling_Intrusion_Detection_System_BMIDS_Using_Internet_of_Things_IoT_Behavior-Based_Anomaly_Detection_via_Immunity-Inspired_Algorithms [Accessed: 08-Mar-2023].doi: 10.1109/ICCCN.2016.7568495 |
| [24] | L. W. ,. T. V. Shahid Raza, “SVELTE: Real-time intrusion detection in the Internet of Things,” Ad Hoc Networks, vol. 11, no. 08, p. 2674, 17 May 2013. [Online]. Available:https://www.sciencedirect.com/science/article/abs/pii/S1570870513001005 [Accessed: 16-Mar-2023].doi: https://doi.org/10.1016/j.adhoc.2013.04.014[Accessed: 06-Mar-2023]. |

Leave a comment