
Contents
In the ever-evolving landscape of cyber threats, one menace has grown increasingly prevalent and dangerous: ransomware. This malicious software, designed to encrypt data and demand payment for its release, has become a significant threat to individuals, businesses, and even government agencies. Understanding what ransomware is and how it operates is the first step in defending against it.
High-Profile Ransomware Attacks. 3
Ransomware’s impact can be devastating. High-profile cases, such as the WannaCry attack that crippled the UK’s National Health Service and the NotPetya attack that caused billions of dollars in damages globally, highlight the destructive potential of these attacks. These incidents demonstrate that no one is immune, emphasizing the need for robust cybersecurity measures.
Ransomware typically infiltrates systems through deceptive methods. Phishing emails, which trick users into downloading malicious attachments or visiting compromised websites, are a common vector. Attackers also exploit software vulnerabilities, especially in systems that are not regularly updated. Understanding these tactics is crucial in developing strategies to prevent infection.
Preventing ransomware infections involves multiple layers of defense. 5
- Regular Backups: Keep regular backups of all critical data. These backups should be stored separately from your main system to prevent them from being encrypted during a ransomware attack.
- Software Updates: Regularly updating software can close security gaps that ransomware exploits.
- Employee Education: Since human error often leads to ransomware infections, educating employees about phishing and other deceptive practices is vital.
- Antivirus and Anti-Malware Tools: Use reliable security solutions to detect and block ransomware.
Responding to a Ransomware Attack. 7
If you fall victim to a ransomware attack, the recommended response is to avoid paying the ransom. Paying does not guarantee data recovery and may encourage further criminal activity. Instead, disconnect the infected systems from your network to prevent the spread of the ransomware, and contact cybersecurity professionals.
Ransomware is continually evolving, with newer forms targeting mobile devices and IoT (Internet of Things) technologies. As artificial intelligence and machine learning become more sophisticated, they could either bolster defense mechanisms or lead to more intelligent ransomware attacks.
The rise of ransomware is a reminder of the constant vigilance required in the digital age. By understanding the threat, implementing robust security measures, and fostering a culture of cybersecurity awareness, individuals and organizations can significantly reduce their vulnerability to these crippling attacks. Stay informed, stay prepared, and remember, the best defense is a proactive one.
Introduction to Ransomware
Ransomware is a type of malicious software that has become one of the most significant and pervasive cyber threats in the digital age. At its core, ransomware is designed to covertly encrypt data on a victim’s device, rendering it inaccessible. The attackers then demand a ransom, typically in cryptocurrency, for the decryption key. This digital extortion has proven to be a lucrative and increasingly popular tactic among cybercriminals.
The concept of ransomware is not new, but its methods and targets have evolved significantly over the years. Initially, ransomware attacks were relatively basic, often locking users out of their systems and displaying a message demanding payment to regain access. However, modern ransomware is far more sophisticated, using advanced encryption algorithms to lock away critical files and data, making them inaccessible even to tech-savvy users.
The impact of ransomware extends beyond individual inconvenience; it poses a severe threat to businesses and organizations of all sizes. Critical data, customer information, and operational capabilities can be compromised, leading to substantial financial losses and damage to reputation. High-profile attacks on public infrastructure, healthcare systems, and government agencies have highlighted the potential for widespread disruption.
Ransomware typically spreads through phishing emails, malicious attachments, or by exploiting vulnerabilities in software. Once inside a network, it can propagate quickly, encrypting files across multiple devices and often evading detection until the damage is done.
Understanding ransomware and its tactics is crucial in the modern digital landscape. Awareness, coupled with robust cybersecurity practices, is key to defending against these insidious attacks. In the following sections, we’ll delve deeper into how ransomware operates, its consequences, and the most effective strategies for prevention and response.
High-Profile Ransomware Attacks
High-profile ransomware attacks have demonstrated the severe impact and widespread disruption that this form of cybercrime can cause. These incidents have not only resulted in significant financial losses but also highlighted the vulnerabilities in cybersecurity measures across various sectors. Here are some notable ransomware attacks that have made headlines:
- WannaCry (2017)
One of the most infamous ransomware attacks, WannaCry, affected over 200,000 computers across 150 countries. It targeted computers running Microsoft Windows by encrypting data and demanding ransom payments in Bitcoin. The attack was particularly notable for its impact on the UK’s National Health Service (NHS), causing widespread disruption to hospital systems and patient care.
- NotPetya (2017)
Shortly after WannaCry, the NotPetya attack emerged, causing massive disruptions globally. It initially targeted organizations in Ukraine, including banks, ministries, newspapers, and electricity firms, but quickly spread worldwide. NotPetya was unique because it was designed more to disrupt than to collect ransom, leading to extensive damage to the infected systems.
- Colonial Pipeline (2021)
The Colonial Pipeline attack in the United States was a significant example of how ransomware could impact critical infrastructure. The attack forced the company to shut down approximately 5,500 miles of pipeline, leading to a spike in gas prices, panic buying, and widespread fuel shortages in the Southeastern United States.
- Baltimore City Government (2019)
The city government of Baltimore, Maryland, faced a major ransomware attack that encrypted thousands of its computers and servers. The attack disrupted numerous city services, including real estate transactions, and cost the city over $18 million in recovery and lost revenue.
- Garmin (2020)
Garmin, a multinational technology company, was hit by a ransomware attack that disrupted its website, customer support, user data synchronization, and other services. The incident highlighted the vulnerability of technology companies to such attacks.
These high-profile attacks underscore the importance of robust cybersecurity measures and the need for proactive strategies to prevent ransomware infections. They also demonstrate that no sector is immune – from healthcare and government to critical infrastructure and technology companies, the threat of ransomware is ubiquitous and demands constant vigilance.
How Ransomware Spreads
Understanding how ransomware spreads is crucial in developing effective strategies to prevent these attacks. Ransomware typically infiltrates systems through various methods, often relying on user interaction or exploiting system vulnerabilities. Here are the common ways ransomware spreads:
- Phishing Emails
One of the most common methods of ransomware distribution is through phishing emails. These emails appear to be from legitimate sources and trick users into clicking on malicious links or downloading infected attachments. Once the user interacts with these elements, the ransomware is deployed onto their system.
- Malvertising
Malvertising involves embedding malware in online advertisements. Users can inadvertently initiate a ransomware download by clicking on these ads, even on reputable websites, if the site’s ad network has been compromised.
- Exploit Kits
These are tools used by cybercriminals to exploit known vulnerabilities in software and systems. When a user with an unpatched vulnerability visits a compromised website, the exploit kit can automatically download and install the ransomware.
- Drive-By Downloads
In drive-by download attacks, ransomware is downloaded and installed in the background without the user’s knowledge, typically when they visit a malicious or compromised website.
- Social Engineering Tactics
Beyond phishing, other forms of social engineering tactics are used to trick users into installing ransomware. This may include fake software updates or bogus tech support scams.
- Remote Desktop Protocol (RDP) Attacks
Ransomware can also spread through Remote Desktop Protocol (RDP) attacks, where attackers exploit weak or stolen RDP credentials to gain access to a network and deploy ransomware.
- Network Propagation
Once ransomware infects one machine in a network, it can often spread to other interconnected systems and devices. This is particularly dangerous in organizational networks where many systems are interconnected.
- USB and Other Removable Media
Ransomware can also be spread through USB drives or other removable media. If an infected USB drive is plugged into a different computer, the ransomware can execute and infect the new system.
- File-Sharing Networks
Using file-sharing services or peer-to-peer networks can also be a risk factor, as ransomware can be disguised as legitimate files and downloaded by unsuspecting users.
By being aware of these distribution methods, individuals and organizations can take proactive steps to protect themselves from ransomware attacks. This includes implementing security best practices such as regularly updating software, training employees on cybersecurity awareness, and using reputable antivirus and anti-malware solutions.
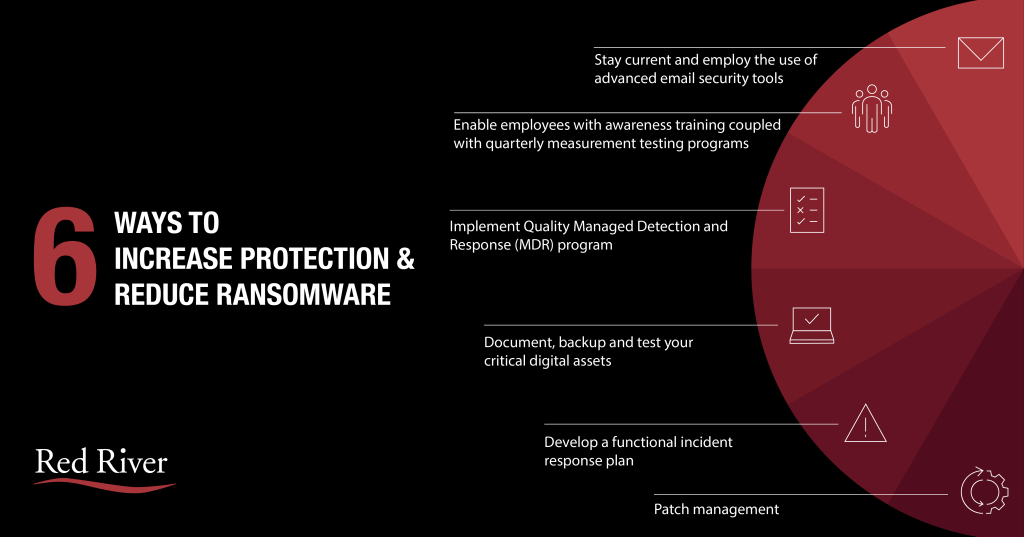
Preventing ransomware infections involves multiple layers of defense.

Preventing ransomware infections indeed requires a multi-layered defense strategy. No single solution is foolproof, so combining several protective measures significantly enhances security. Here’s how to build a robust defense against ransomware:
- Regular Data Backups
Regularly back up all critical data, ensuring backups are not connected to your primary network. Using cloud services or external storage devices for backups can prevent them from being encrypted during a ransomware attack.
- Timely Software Updates
Keep all software, especially operating systems, and antivirus programs, up to date. Regular updates often include patches for security vulnerabilities that ransomware could exploit.
- Use Antivirus and Anti-Malware Software
Install and maintain reputable antivirus and anti-malware software. These tools can detect and quarantine ransomware before it causes harm.
- Employee Training and Awareness
Conduct regular training sessions for employees on cybersecurity best practices. Educate them about the dangers of phishing emails, suspicious links, and unverified downloads.
- Email Filtering and Security
Implement advanced email filtering to block malicious emails and attachments. This reduces the likelihood of phishing attacks reaching end-users.
- Network Segmentation
Divide your network into subnetworks to limit the spread of ransomware if one segment gets infected. This helps contain the threat and minimizes damage.
- Strong Password Policies
Enforce strong, unique passwords for all accounts and change them regularly. Implement multi-factor authentication (MFA) for an additional layer of security.
- Limit User Access and Privileges
Apply the principle of least privilege by limiting user access rights. Users should only have the access necessary to perform their job.
- Regular Security Audits and Vulnerability Assessments
Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses in your network.
- Disaster Recovery Planning
Develop and maintain a disaster recovery plan. This plan should outline procedures to follow in the event of a ransomware attack, ensuring quick and effective response.
- Secure Remote Access
Use Virtual Private Networks (VPNs) and ensure secure configurations for remote access systems like Remote Desktop Protocol (RDP).
- Patch Management
Implement a robust patch management policy to ensure all software is up-to-date and vulnerabilities are patched promptly.
- Application Whitelisting
Only allow approved applications to run on your network, which can prevent unauthorized applications, including ransomware, from executing.
- Monitor and Respond
Continuously monitor your network for suspicious activities and have an incident response plan ready to swiftly address potential threats.
By implementing these measures, you can significantly bolster your defenses against ransomware and mitigate the risk of a successful attack. Remember, cybersecurity is an ongoing process, requiring constant vigilance and adaptation to emerging threats.
Responding to a Ransomware Attack
Responding effectively to a ransomware attack is crucial in minimizing damage and restoring operations. Here’s a guide on how to respond if your system is compromised by ransomware:
- Isolate the Infected Systems
Immediately disconnect the infected devices from all networks, including wireless and wired connections, and isolate them to prevent the spread of ransomware to other devices. If possible, remove or disconnect any external storage devices as well.
- Identify the Ransomware Variant
Determine the type of ransomware you are dealing with. Some ransomware variants display a message with a name or instructions. Identifying the ransomware can help in understanding its behavior and potential decryption methods.
- Secure Your Backups
Ensure that your backups are secure and uninfected. Do not connect backup drives or access backup files until you are sure they are safe from ransomware.
- Engage Cybersecurity Professionals
Contact IT professionals or a cybersecurity firm specializing in ransomware response. They can provide expertise in managing the attack, mitigating damage, and possibly decrypting files.
- Notify Relevant Authorities
Report the ransomware attack to law enforcement. Agencies like the FBI or your country’s cybercrime unit can provide support and may have information about the specific ransomware variant.
- Assess the Damage and Impact
Evaluate the extent of the infection and the impact on your operations. Identify which systems and data are affected and to what extent.
- Do Not Pay the Ransom
The general advice from cybersecurity experts is to avoid paying the ransom. Paying does not guarantee file recovery and encourages further criminal activity. In some jurisdictions, paying ransom to certain organizations is illegal.
- Attempt Decryption and Recovery
Check for available decryption tools. Some cybersecurity firms and law enforcement agencies release decryption tools for certain ransomware variants. If your files were backed up, plan for data recovery from these backups.
- Communicate the Incident
Inform stakeholders, including employees, customers, and partners, about the breach, especially if sensitive data is involved. Transparency is crucial for maintaining trust and managing reputational risk.
- Conduct a Post-Incident Analysis
After resolving the immediate crisis, conduct a thorough analysis of the incident. Determine how the ransomware entered your network, what vulnerabilities were exploited, and assess your response to the attack.
- Improve and Update Security Measures
Use the insights gained from the attack to strengthen your cybersecurity posture. Update your security protocols, improve employee training, and implement more robust backup and recovery procedures.
- Develop a Response Plan for Future Incidents
Prepare or update an incident response plan based on the lessons learned. This plan should outline specific steps to take in the event of future ransomware or other cyber-attacks.
Responding to a ransomware attack can be a challenging and stressful process. Quick and coordinated actions, coupled with professional assistance, can help mitigate the effects of the attack and pave the way for a more secure IT environment moving forward.
The Future of Ransomware
The future of ransomware looks to be an evolving landscape, shaped by technological advancements and the ever-changing tactics of cybercriminals. As we look ahead, several trends and predictions are likely to define the trajectory of ransomware threats:
- Targeting Critical Infrastructure
Ransomware attacks are expected to increasingly target critical infrastructure sectors, such as healthcare, energy, and public utilities. These targets are often seen as more likely to pay ransoms due to the critical nature of their services.
- Advanced Evasion Techniques
Cybercriminals will likely develop more sophisticated ransomware variants that are harder to detect and counter. These may include polymorphic ransomware that changes its own code to evade detection or ransomware that can bypass traditional antivirus solutions.
- Use of Artificial Intelligence and Machine Learning
Both attackers and defenders are expected to leverage AI and machine learning. Attackers might use these technologies to automate attacks, identify lucrative targets, and customize ransom demands. On the flip side, AI could help in predicting and quickly responding to ransomware attacks.
- Exploitation of IoT Devices
As the Internet of Things (IoT) continues to expand, so does the attack surface for ransomware. IoT devices, often less secure, could be targeted to disrupt everyday life or as entry points into larger networks.
- Ransomware-as-a-Service (RaaS)
The RaaS model, where ransomware tools are rented out like a subscription service, is likely to grow. This makes it easier for individuals without extensive technical knowledge to launch ransomware attacks, potentially increasing the frequency of these attacks.
- Double Extortion and Beyond
The tactic of double extortion, where attackers both encrypt data and threaten to release it publicly, is expected to evolve. Future ransomware attacks might involve additional threats, like disrupting operations or targeting clients of the victim company.
- More Targeted Ransomware Attacks
Instead of widespread attacks, future ransomware campaigns might be more targeted, focusing on specific organizations or industries with a higher likelihood of paying larger ransoms.
- Legal and Regulatory Responses
As ransomware becomes a more significant threat, expect more robust legal and regulatory responses. This may include stricter regulations around cybersecurity practices and reporting of ransomware incidents.
- Increased Public Awareness and Preparedness
Public awareness about ransomware is expected to grow, leading to better preparedness and more robust cybersecurity practices both at individual and organizational levels.
- Integration with Other Types of Attacks
Ransomware may be combined with other forms of cyberattacks, like data breaches or DDoS (Distributed Denial of Service) attacks, to maximize impact.
The future of ransomware presents significant challenges but also opportunities for advancements in cybersecurity. It underscores the need for continuous vigilance, investment in advanced security measures, and a proactive approach to cyber threats. As the landscape evolves, so must our strategies to defend against these pervasive and damaging attacks.
Conclusion
In conclusion, the rise of ransomware represents a significant and evolving challenge in the world of cybersecurity. This form of digital extortion has proven not only to be a lucrative venture for cybercriminals but also a major threat to individuals, businesses, and even national security. The increasing sophistication of ransomware attacks calls for a robust and multi-faceted approach to cybersecurity.
As we have seen, ransomware can cripple critical infrastructure, lead to substantial financial losses, and compromise sensitive data. The key to combating this threat lies in a combination of preparedness, education, and the implementation of strong security measures. Regular data backups, updated security systems, employee awareness, and a swift response plan are essential components of a comprehensive defense strategy.
Moreover, the future landscape of ransomware suggests an arms race between cybercriminals and cybersecurity professionals. The use of advanced technologies like AI and machine learning in ransomware attacks will likely prompt an equivalent response in defense mechanisms. The expanding IoT network, growing reliance on digital infrastructures, and the increasing sophistication of cyber attacks underscore the need for continuous vigilance and adaptation in cybersecurity practices.
In navigating the challenges posed by ransomware, collaboration and information sharing between organizations, cybersecurity experts, and law enforcement agencies play a critical role. Staying informed about the latest ransomware trends and protective measures is crucial for all digital users.
Ultimately, the rise of ransomware is a reminder of the importance of cybersecurity in the digital age. By understanding the threat, being proactive in defense strategies, and remaining vigilant, we can protect our digital assets and maintain the integrity of our digital ecosystems. The battle against ransomware is ongoing, but with the right tools and awareness, it is one that can be fought effectively.
Top of Form

Leave a comment