Contents
In the landscape of cybersecurity, protecting network authentication is paramount. Kerberos, an authentication protocol, plays a vital role in this domain. Understanding how Kerberos enhances network security is crucial for any IT professional or organization concerned with protecting their digital assets.
Developed at MIT in the 1980s, Kerberos is a network authentication protocol designed to provide strong authentication for client-server applications using secret-key cryptography. Its name, derived from Greek mythology’s guardian of the underworld, aptly reflects its role in safeguarding network access.
Kerberos operates on a ticket-based system. The process involves three main components: the client, the Key Distribution Center (KDC), and the server. Here’s a simplified breakdown:
- Authentication Request: The client requests an authentication ticket (TGT) from the KDC.
- Ticket Granting Ticket (TGT): If the client’s credentials are valid, the KDC issues a TGT and a session key.
- Service Request: The client uses the TGT to request a service ticket for the desired server.
- Accessing the Service: The server verifies the service ticket and grants access.
Benefits of Kerberos in Cybersecurity. 5
- Strong Authentication: By using tickets and encrypted keys, Kerberos ensures that user credentials are never transmitted over the network, reducing the risk of interception.
- Mutual Authentication: Both the client and server verify each other’s identities, adding an extra layer of security.
- Delegated Authentication: Kerberos can securely delegate user rights, enabling secure service-to-service communications.
- Time-Sensitive Tickets: The time-limited validity of tickets reduces the risk of replay attacks.
Kerberos in Modern Networks. 6
In today’s digital environment, Kerberos is integral to various systems, particularly in Windows Active Directory environments. It’s also compatible with UNIX and Linux systems, making it a versatile choice for diverse network architectures.
Challenges and Considerations. 8
While Kerberos is robust, it’s not without challenges. Network administrators must ensure proper configuration and regular updates to prevent vulnerabilities. Additionally, Kerberos requires a reliable time source for all entities in the network, as discrepancies can lead to authentication failures.
Best Practices for Implementing Kerberos. 9
- Regular Updates: Keep your Kerberos implementation up to date with the latest security patches.
- Secure KDC: The Key Distribution Center should be highly secure, as it’s a critical component.
- Educate Users: Ensure that users understand the importance of safeguarding their credentials.
- Monitor and Audit: Regularly monitor and audit Kerberos authentication logs for unusual activities.
The Future of Kerberos in Cybersecurity. 11
As cyber threats evolve, Kerberos continues to adapt. Its integration into cloud services and potential enhancements, like stronger encryption and better token management, will ensure its relevance in the cybersecurity landscape.
Kerberos remains a cornerstone in network security, offering a robust framework for protecting authentication processes. By understanding and properly implementing Kerberos, organizations can significantly bolster their network’s defense against a range of cyber threats, ensuring that their digital environments remain secure and trustworthy.

Introduction
In the ever-evolving field of cybersecurity, one of the most critical aspects is safeguarding network authentication. This is where Kerberos, a time-tested authentication protocol, emerges as a key player. For IT professionals and organizations deeply invested in the security of their digital infrastructure, a thorough understanding of Kerberos is not just beneficial but essential.
Kerberos, developed at the Massachusetts Institute of Technology (MIT), is designed to strengthen the security of client-server applications through secret-key cryptography. This approach ensures that sensitive information, particularly user credentials, is not exposed during the authentication process. In an age where cyber threats are increasingly sophisticated and pervasive, Kerberos provides a robust defense mechanism, ensuring that only authenticated users gain access to network resources.
The significance of Kerberos extends beyond its technical capabilities. It represents a fundamental component in a broader strategy to fortify networks against unauthorized access and potential breaches. As we delve deeper into the workings of Kerberos and its role in contemporary cybersecurity, it becomes clear why this protocol is a cornerstone in network defense strategies for countless organizations around the globe.
Understanding Kerberos is more than just a technical requirement; it’s a strategic imperative in the quest to protect network integrity and maintain trust in digital systems. This introduction sets the stage for a comprehensive exploration of how Kerberos operates, its benefits in the cybersecurity landscape, and the best practices for its implementation and maintenance.
What is Kerberos?
Originating from the Massachusetts Institute of Technology (MIT) in the 1980s, Kerberos stands as a pivotal authentication protocol within the realm of network security. Its inception was aimed at resolving the inherent security challenges in the burgeoning field of digital networks, particularly in client-server applications.
Kerberos employs secret-key cryptography to facilitate secure authentication processes. This method ensures that sensitive user credentials are protected during the authentication phase of accessing network services. The protocol operates based on a ticketing system, which authorizes users without transmitting their actual password over the network.
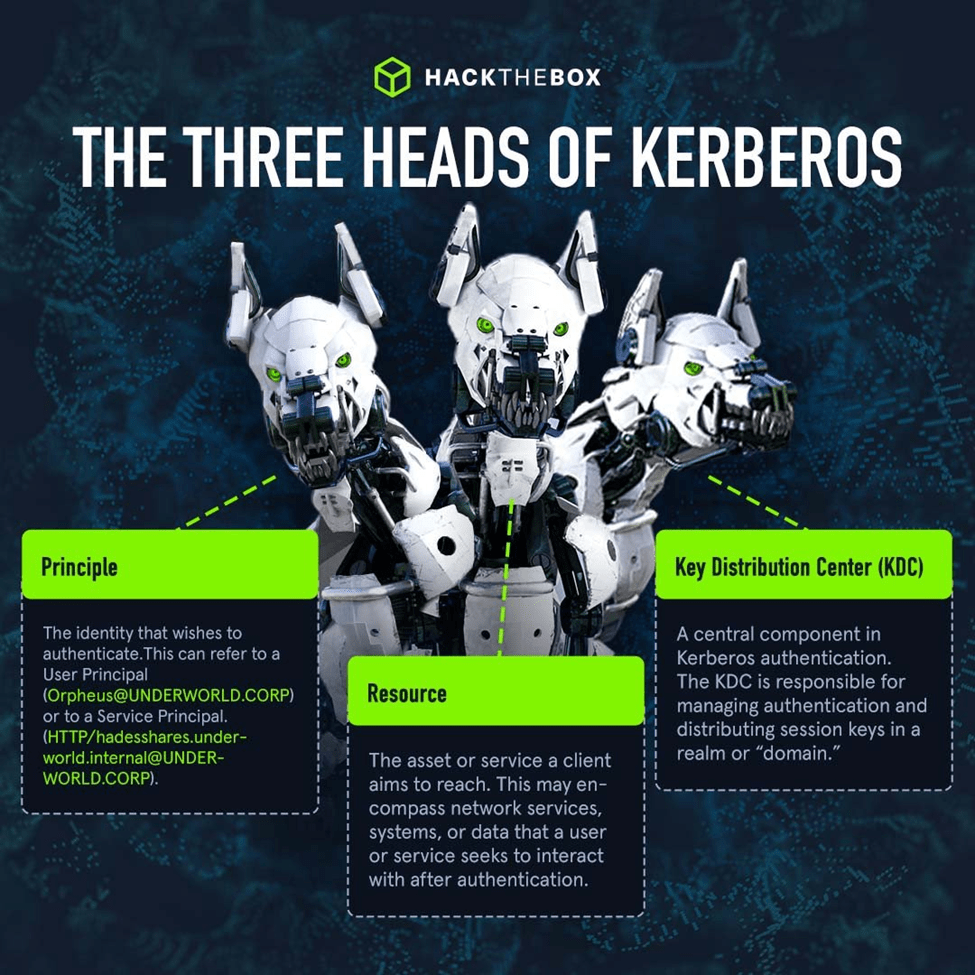
The choice of the name “Kerberos” is deeply symbolic. Drawing from Greek mythology, where Kerberos (or Cerberus) is depicted as the three-headed dog guarding the gates of the underworld, the protocol serves a similar purpose in the digital world. It stands as the guardian at the gates of network access, ensuring that only authenticated and authorized entities can gain entry.
At its core, Kerberos is designed to address the challenges of secure user authentication in distributed environments. It is particularly adept at managing authentication in large and complex network infrastructures where traditional methods, like password-based authentication, fall short in terms of security and scalability.
The protocol’s architecture, which revolves around the use of tickets and secret keys, has proven to be highly effective in mitigating a range of security risks, such as eavesdropping and replay attacks. As a result, Kerberos has become a fundamental component in the security strategies of many organizations, underpinning the secure operations of myriad networked systems and applications.
In summary, Kerberos is not just a technical solution; it’s a cornerstone of modern network security practices, providing a robust and reliable framework for safeguarding network access in an increasingly interconnected and digitalized world.
How Kerberos Works
Kerberos, renowned for its robust security framework, operates on an ingenious ticket-based system. This system is meticulously designed to ensure secure authentication in client-server environments. Central to this process are three key components, the client, the Key Distribution Center (KDC), and the server. Let’s explore each step in this process to understand how Kerberos manages to maintain high security standards.
Authentication Request
- Step 1 – Initiating Contact
It all begins when the client initiates a request for authentication. This request is directed towards the Key Distribution Center (KDC). In essence, the client is asking KDC for a way to prove its identity in a secure manner across the network.
Ticket Granting Ticket (TGT)
- Step 2 – Validating Credentials
Upon receiving the request, the KDC first verifies the client’s credentials. If the credentials are deemed valid, the KDC proceeds to issue a Ticket Granting Ticket (TGT).
- The Role of the TGT
The TGT is an encrypted ticket that the client uses to request access to various services within the network.
- Issuance of the Session Key
Alongside TGT, the client also receives a session key. This key plays a crucial role in establishing a secure communication channel between the client and the service it wants to access.
Service Request
- Step 3 – Requesting Service Access
Armed with the TGT, the client now approaches the KDC again, this time to request access to a specific server (service) within the network. The client uses TGT to prove its identity and to demonstrate that it has been authenticated previously.
- Granting a Service Ticket
If the TGT is valid, the KDC issues a service ticket. This ticket is specifically meant for the server (service) that the client wants to access.
Accessing the Service
- Step 4 – Gaining Access
Finally, the client presents this service ticket to the desired server.
- Verification by the Server
The server verifies the service ticket. This verification is critical as it ensures that the ticket is valid and has been issued by the KDC.
- Granting Access
Once the server is satisfied with the authenticity of the service ticket, it grants access to the client.
This process, with its emphasis on tickets and encryption, ensures that the client’s credentials are never exposed directly over the network, significantly reducing the risk of credential theft or interception. The use of session keys and time-limited tickets further enhances the security of the entire system, making Kerberos one of the most secure authentication protocols in use today.
In summary, Kerberos excels at providing a secure and efficient way for clients to prove their identity to servers across an insecure network, thereby upholding the integrity and confidentiality of sensitive authentication data.
Benefits of Kerberos in Cybersecurity

Kerberos, a pivotal authentication protocol, brings a multitude of benefits to the field of cybersecurity. These benefits are rooted in its unique architecture and operational model, which focuses on safeguarding network communication and ensuring secure authentication. Let’s delve into the key advantages that Kerberos offers,
Strong Authentication
- Ticket-Based Mechanism
Kerberos employs a sophisticated ticket-based system for authentication. This approach ensures that sensitive user credentials are not transmitted over the network during the authentication process.
- Encrypted Keys
The use of encrypted keys in the Kerberos protocol significantly reduces the risk of credential interception. These keys offer a secure method for clients and servers to establish trust and verify identity.
Mutual Authentication
- Two-Way Verification
Kerberos introduces an additional layer of security through mutual authentication. This means that not only does the client need to prove its identity to the server, but the server also needs to prove its identity to the client.
- Enhanced Trust
This bi-directional verification process reinforces the overall security of network communications, ensuring that both parties are indeed who they claim to be.
Delegated Authentication
- Safe Delegation of Rights
Kerberos has the capability to securely delegate user rights. This feature is particularly valuable in complex network environments where services need to communicate with each other on behalf of users.
- Seamless Service-to-Service Communication
By enabling secure delegation, Kerberos facilitates safe and efficient service-to-service communications, which is a crucial aspect of modern networked systems.
Time-Sensitive Tickets
- Limited Validity
One of the defining features of Kerberos is the time-limited validity of its tickets. These tickets are only valid for a predetermined period, which is typically configured based on security requirements.
- Reduced Risk of Replay Attacks
The temporal limitation of tickets greatly diminishes the risk of replay attacks. In such attacks, a valid data transmission is maliciously or fraudulently repeated or delayed. With time-sensitive tickets, the window for such attacks is significantly narrowed.
In summary, the Kerberos authentication protocol offers robust security features that are essential in the current cybersecurity landscape. Its ability to provide strong and mutual authentication, safely delegate user rights, and minimize the risks of replay attacks through time-sensitive tickets makes it an invaluable tool in securing networked environments. These benefits underscore why Kerberos continues to be a trusted and widely implemented solution in the realm of network security.
Kerberos in Modern Networks
Kerberos has evolved to become a fundamental element in the security architecture of modern digital networks. Its widespread adoption and integration into various systems underscore its versatility and effectiveness in addressing contemporary cybersecurity needs. Let’s explore how Kerberos plays a pivotal role in today’s network environments.
Kerberos in Windows Active Directory Environments
- Seamless Integration
In Windows environments, particularly those using Active Directory (AD), Kerberos is seamlessly integrated. It serves as the default authentication protocol for the Windows operating system since Windows 2000.
- Centralized Authentication
Kerberos provides a centralized authentication mechanism in Active Directory, enabling users to access multiple services across the network without needing to re-authenticate.
- Enhanced Security
By leveraging Kerberos, Windows networks benefit from stronger security features, such as mutual authentication and encrypted data exchange, enhancing overall network security.
Compatibility with UNIX and Linux Systems
- Cross-Platform Support
Beyond Windows environments, Kerberos exhibits strong compatibility with UNIX and Linux systems. This cross-platform support is crucial for organizations operating in heterogeneous network environments.
- Flexibility in Integration
Kerberos can be integrated into various UNIX and Linux distributions, offering a consistent and secure authentication mechanism across different platforms.
- Support for Legacy Systems
Kerberos’ compatibility extends to legacy systems as well, providing a bridge between new and old technologies, which is essential for gradual tech upgrades in large organizations.
Diverse Network Architectures
- Adaptability
Kerberos is designed to adapt to a wide range of network architectures, from small local networks to large-scale distributed systems.
- Scalability
Its scalability is a significant advantage, allowing it to handle the authentication needs of networks that are expanding in size and complexity.
- Hybrid Environments
With the rise of cloud computing, Kerberos proves to be a vital component in hybrid environments, efficiently managing authentication across on-premises and cloud-based resources.
The Role of Kerberos in Emerging Technologies
- Cloud Computing
As organizations move towards cloud-based solutions, Kerberos plays a critical role in securing access to cloud services and applications.
- Internet of Things (IoT)
With the expanding realm of IoT, Kerberos is being adapted to secure communications between IoT devices and networks, ensuring authenticated and authorized access.
In conclusion, Kerberos has effectively evolved to meet the demands of modern network infrastructures. Its integral role in Windows Active Directory environments, compatibility with UNIX and Linux systems, and adaptability to diverse network architectures and emerging technologies highlight its enduring relevance and criticality in today’s digital landscape. Kerberos continues to be a cornerstone in the pursuit of robust and scalable network security solutions.
Challenges and Considerations
Kerberos, despite its strengths in network security, presents certain challenges and considerations that must be addressed to ensure its effectiveness. Understanding and managing these aspects is critical for network administrators and IT professionals. Here’s a closer look at some of these challenges and considerations.
Configuration Complexity
- Proper Setup
Kerberos requires meticulous configuration to function correctly. Incorrect setup can lead to vulnerabilities or operational issues.
- Administrative Overhead
The complexity of Kerberos configuration can result in a higher administrative burden, especially in large and diverse network environments.
Regular Updates and Maintenance
- Staying Updated
Regular updates are essential to maintain the security integrity of Kerberos. Outdated systems may be susceptible to newer types of cyber threats.
- Patch Management
Effective patch management policies are necessary to address any vulnerabilities in a timely manner, ensuring the Kerberos system remains secure against evolving threats.
Time Synchronization
- Critical Dependency on Time
Kerberos is heavily reliant on time synchronization across all network entities. This is because the tickets Kerberos issues are time-stamped for security.
- Time Discrepancies
Any significant time discrepancy between the client, the KDC, and the server can lead to authentication failures. Therefore, maintaining a synchronized and reliable time source is crucial.
Scalability and Performance
- Handling Large Networks
In large-scale deployments, Kerberos must be scaled appropriately to handle the increased load without compromising performance.
- Resource Allocation
Ensuring adequate resources and infrastructure to support Kerberos, especially in rapidly growing network environments, is essential.
Interoperability with Other Systems
- Compatibility Issues
Kerberos needs to be compatible with various operating systems and applications. In heterogeneous environments, ensuring seamless interoperability can be challenging.
- Integration with Legacy Systems
Integrating Kerberos with older systems or non-standard applications often requires additional effort and customization.
Security Considerations
- Single Point of Failure
The Key Distribution Center (KDC) in Kerberos is a critical component. If compromised or unavailable, it can impact the entire authentication process.
- Protection of the KDC
Securing the KDC against attacks and ensuring its availability is paramount, as it is the heart of the Kerberos authentication process.
Adaptation to New Technologies
- Evolving Cyber Threats
Kerberos must continuously adapt to counter new and sophisticated cyber threats.
- Emerging Technologies
The rise of cloud computing, IoT, and other emerging technologies presents new challenges for Kerberos integration and security.
In summary, while Kerberos is a powerful tool for securing network authentication, its effective implementation and maintenance require careful consideration of various challenges. Addressing these considerations is vital for leveraging the full potential of Kerberos in enhancing network security.
Best Practices for Implementing Kerberos
Implementing Kerberos in a network environment involves more than just setting up the protocol; it requires ongoing vigilance and adherence to best practices to ensure its effectiveness and security. Here are some key best practices that should be followed when implementing Kerberos.
Regular Updates
- Stay Current with Patches
Regularly update your Kerberos implementation with the latest security patches. This is crucial for protecting against new vulnerabilities as they are discovered.
- Scheduled Maintenance
Establish a routine schedule for checking and applying updates and patches to ensure that your Kerberos environment remains secure.
Secure the Key Distribution Center (KDC)
- Robust Security Measures
Given its critical role in the Kerberos authentication process, the KDC must be highly secure. Implement strong security measures to protect it from potential attacks.
- Restricted Access
Limit access to the KDC to only those administrators who absolutely need it, reducing the risk of internal threats or accidental misconfigurations.
Educate Users
- Awareness Training
Educate users about the importance of protecting their credentials. Users are often the weakest link in security, and informed users are less likely to fall prey to social engineering attacks.
- Best Practices for Passwords
Encourage strong password practices, such as using complex passwords and changing them regularly.
Monitor and Audit
- Regular Monitoring
Continuously monitor Kerberos authentication logs for any unusual or suspicious activities. This can help in quickly identifying potential security breaches or issues.
- Audit Trails
Maintain comprehensive audit trails of authentication attempts and changes to the Kerberos configuration. This is essential for tracking the cause in case of a security incident.
Additional Best Practices
- Time Synchronization
Ensure that all servers and clients in the network are synchronized with the same time source. Time discrepancies can cause authentication failures in Kerberos.
- Backup and Recovery
Regularly back up the Kerberos database and have a recovery plan in place. This is crucial for restoring the service in case of a system failure or breach.
- Plan for Scalability
Consider the scalability of your Kerberos implementation, especially if you expect growth in your network or an increase in authentication requests.
- Test Your Setup
Regularly test your Kerberos setup to ensure that it is functioning as intended and to identify any potential issues before they become problematic.
By following these best practices, organizations can significantly enhance the security and reliability of their Kerberos implementation, ensuring robust protection for their network environments.
The Future of Kerberos in Cybersecurity
Kerberos, with its robust framework, has stood the test of time in the realm of network security. As we navigate through an era of rapidly evolving cyber threats, Kerberos is not static; it’s evolving to meet these new challenges head-on. Let’s explore what the future holds for Kerberos in the cybersecurity landscape.
Enhanced Encryption Standards
- Stronger Cryptographic Techniques
As computational power increases, Kerberos is expected to adopt even stronger encryption methods to safeguard against advanced decryption techniques and quantum computing threats.
- Dynamic Encryption Algorithms
The future may see Kerberos implementing more dynamic, adaptable encryption algorithms that can be updated or changed based on the prevailing security requirements.
Integration with Cloud Services
- Cloud-Based Authentication
With the shift towards cloud computing, Kerberos is increasingly being integrated into cloud services for secure authentication.
- Hybrid Environments
Kerberos is expected to play a crucial role in bridging on-premises and cloud environments, ensuring secure authentication across diverse infrastructures.
Improved Token Management
- Advanced Token Security
Future developments in Kerberos may focus on enhancing the security and management of tokens, making them more resilient to theft and misuse.
- Seamless Token Lifecycle Management
Improvements in the way Kerberos handles token issuance, expiration, and renewal are anticipated, contributing to smoother and more secure authentication processes.
Adaptation to Emerging Technologies
- Internet of Things (IoT)
As IoT becomes more prevalent, Kerberos is likely to adapt to secure the vast network of interconnected devices, ensuring authenticated and authorized device communication.
- Mobile Security
With the increasing use of mobile devices in corporate environments, Kerberos might see adaptations or extensions to better support mobile authentication and security needs.
Addressing New Threats
- Anticipating Cyber Threats
Kerberos developers and the cybersecurity community will continue to monitor emerging threats, adapting the protocol to counteract new attack vectors.
- Proactive Security Measures
Future iterations of Kerberos could include more proactive security measures, like advanced anomaly detection and automated threat response mechanisms.
Research and Development
- Continuous Innovation
Ongoing research and development efforts are expected to drive the evolution of Kerberos, focusing on enhancing its efficiency, scalability, and security features.
- Community and Open-Source Contributions
The active community and open-source development model surrounding Kerberos will play a significant role in its future advancements and widespread adoption.
In conclusion, the future of Kerberos in cybersecurity looks promising and dynamic. Its ability to adapt to new technologies, enhanced encryption, improved token management, and integration with cloud services positions Kerberos as a continuingly relevant and vital component in the cybersecurity toolkit for years to come. As the digital world evolves, so will Kerberos, ensuring it remains at the forefront of secure authentication solutions.
Conclusion
Kerberos, with its deep roots in the realm of network security, continues to stand as a bulwark against the ever-evolving landscape of cyber threats. Its sophisticated and robust framework for managing authentication processes plays a pivotal role in safeguarding digital environments. The strength of Kerberos lies not only in its technical capabilities but also in its adaptability and resilience over the years.
For organizations navigating the complexities of network security, a thorough understanding and proper implementation of Kerberos are invaluable. By leveraging this protocol, they can significantly enhance their defenses, protecting their networks from a myriad of cyber threats. Kerberos does more than just secure authentication processes; it instills a level of trust and reliability in digital transactions and interactions.
The ongoing evolution of Kerberos, adapting to emerging technologies and threats, ensures its continued relevance in the cybersecurity domain. As digital landscapes become more interconnected and sophisticated, the role of Kerberos as a cornerstone in network security is not just maintained but reinforced. It stands as a testament to the enduring importance of robust, well-designed security protocols in the digital age.
In conclusion, Kerberos represents a critical element in the strategy of organizations to maintain secure, reliable, and trustworthy digital environments. Its continued development and adaptation will undoubtedly play a key role in shaping the future of cybersecurity, making it an essential component of any comprehensive network security plan.
Top of Form
Bottom of Form

Leave a comment