
Abstract
The burgeoning adoption of Infrastructure as Code (IaC) presents a pivotal shift in the management and security of IT infrastructure. This paper delves into the intricacies of IaC security, explicating its operation and contribution to the DevOps discipline through a methodical and structured approach. The paper explains how IaC leverages version control, automated testing, continuous monitoring, and immutable infrastructure to fortify security measures. It underscores the implementation of least privilege access and declarative language to articulate infrastructure state, thus ensuring consistency and adherence to security policies. An architectural diagram is analyzed to delineate the components involved in IaC security, illustrating the collaborative orchestration between source code repositories, CI/CD servers, configuration management tools, and monitoring systems. Real-world applications are explored, demonstrating IaC’s impact on industries like financial services and e-commerce, highlighting the balance of pros and cons in its adoption. The paper accentuates the need for secure coding practices, version control, and continuous compliance to establish robust security measures in the IaC lifecycle. It culminates with insights into the future trajectory of IaC, advocating for a harmonious integration of automated efficiency with stringent security controls to elevate the overall security posture of organizations.
Table of Contents
01. Detailed Explanation of How Infrastructure as Code (IaC) Security Works. 2
How Infrastructure as a Code (IaC) security operates. 2
02. The Architectural Diagram with the Underlying Technologies and Related Industrial Solutions. 3
components involved in IaC security. 3
02.Architectural diagram on automation API or Server in managing infrastructure. 5
Architectural diagram with CI/CD pipeline. 6
Stages in Infrastructure as a Code (IaC) security. 8
03. Real world example on usage or a user case scenario. 10
Secure Cloud Infrastructure for Financial Services. 10
E-commerce Platform Scalability. 11
Applying security measures to Infrastructure as a code. 13
How to ensure IaC security. 14
Pros of Infrastructure as Code (IaC) Security. 16
Cons of Infrastructure as Code (IaC) Security. 17
01. Detailed Explanation of How Infrastructure as Code (IaC) Security Works
Infrastructure as a Code (IaC) security involves managing and provisioning computing infrastructure through machine-readable definition files, rather than physical hardware configuration or interactive configuration tools. It is a key practice within the DevOps discipline, where it helps maintain and secure a large-scale, complex infrastructure through codification.
How Infrastructure as a Code (IaC) security operates.
- Version Control
IaC uses version control systems to keep track of all the changes to the infrastructure. This allows for easy tracking of modifications and reverting to previous states if necessary, enhancing security by ensuring a clear audit trail.
- Automated Testing
With IaC, security tests and compliance checks can be automated. As code is committed, automated tests run to validate the security posture of the infrastructure before it is deployed. [5]
- Continuous Monitoring
IaC supports continuous monitoring of the infrastructure, enabling real-time security postures and quick responses to any anomalies or vulnerabilities that are detected.
- Immutable Infrastructure
IaC can be used to implement immutable infrastructure, where any change is made by replacing the entire infrastructure instead of modifying it. This reduces the risk of persistent threats. [2]
- Least Privilege Access
IaC allows for precise control over who has access to infrastructure management, often implementing the principle of least privilege to minimize security risks.
- Declarative Language
IaC uses a high-level declarative language to define the desired state of the infrastructure, ensuring consistency and adherence to security policies.
02. The Architectural Diagram with the Underlying Technologies and Related Industrial Solutions
components involved in IaC security.
- Source Code Repository
This is depicted as ‘Source Control’. It’s where developers store their application code and the IaC files. Git is a popular tool for this purpose. [4]
- Continuous Integration/Continuous Deployment (CI/CD) Server
The ‘CI/CD Pipeline’ section in the diagram. It takes the code from the source control and automates the testing, building, and deployment of infrastructure changes. Jenkins, Travis CI, and GitLab CI are common tools for these pipelines.
- Configuration Management Tools
These would be part of the ‘Building, Infra Provisioning & Deploying’ step. Ansible, Chef, Puppet, and SaltStack help in setting up and maintaining the desired state of your infrastructure. Automate configuration changes and enforce state. [2]
- IaC Security Scanners
These tools would scan the IaC scripts within the pipeline, ideally before the deployment step, for any security issues. Checkov, Terrascan, and tfsec are examples of such scanners.
- Infrastructure Orchestration Tools
Included in the ‘Building, Infra Provisioning & Deploying’ step, tools like Terraform and AWS CloudFormation are responsible for automating the deployment of the infrastructure.
- Infrastructure Orchestration Tools
These tools automate the deployment of infrastructure. Examples include Terraform and AWS CloudFormation.
- Monitoring and Logging Tools
In the final ‘Prod’ stage, after the infrastructure is deployed, Splunk, Datadog, and ELK Stack would be used for ongoing monitoring and logging to ensure everything is functioning correctly and securely. Collect and analyze data to ensure that the infrastructure is functioning as intended and is secure.
In practice, your IaC files stored in the source code repository define the desired state of your infrastructure. When changes are committed, the CI/CD server automatically triggers the process, using the configuration management tools to set up the infrastructure and orchestration tools to deploy it. Security scanners ensure the changes meet security standards, and once deployed, monitoring tools keep an eye on your live environment.
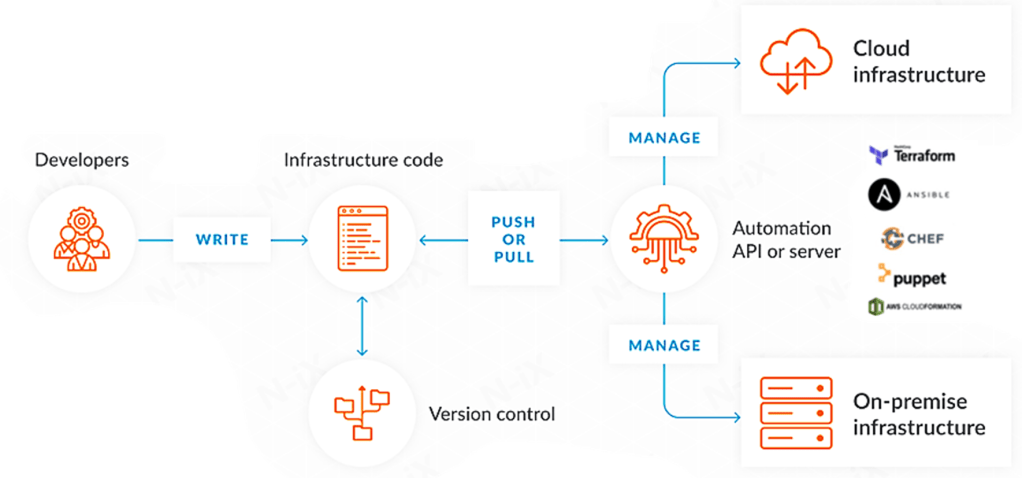
02.Architectural diagram on automation API or Server in managing infrastructure.
Architectural diagram which focuses on the role of the Automation API or Server in managing infrastructure. It shows how this component is central to applying configurations and operational management to both cloud infrastructure and on-premises infrastructure. The key tasks of this component include the execution of infrastructure as code scripts that provision and manage IT resources.

Individuals or teams responsible for writing the infrastructure code.
- Infrastructure Code
This is the codebase that defines the infrastructure setup. It can include server configurations, network topologies, or other infrastructure specifications, all represented in code.
- Version Control
This system, such as Git, is used to track changes to the infrastructure code, allowing for versioning, rollback, and collaboration among different team members.
- Automation API or Server
This represents the automation tools or servers that interface with the cloud or on-premises infrastructure. It receives the infrastructure code and applies it to manage and provision the infrastructure. This could involve APIs from cloud providers like AWS, Azure, or Google Cloud, or automation servers like Jenkins or Bamboo.
- Infrastructure in the Cloud
The cloud-based resources that are provisioned and managed through IaC. This includes virtual machines, networks, storage, and more, hosted on cloud platforms.
- Infrastructure on Premises
This represents any physical or virtual servers, storage, networking, and other IT infrastructure that is located on-premises, within the organization’s own data centers. [4]
The flow indicates that developers write the infrastructure code and push or pull it to version control systems. The automation API or server then takes this code to manage the infrastructure both in the cloud and on-premises, thereby ensuring that the infrastructure setup is consistent with the code definitions. This IaC model allows for reproducibility, scalability, and agility in infrastructure management.
Architectural diagram with CI/CD pipeline
Architectural diagram with CI/CD pipeline, which is more focused on the software development lifecycle. It illustrates how code is built, tested, and then progressed through various environments—development, staging, and production. The CI/CD pipeline automates the processes of integration, testing, building, and deploying software changes.
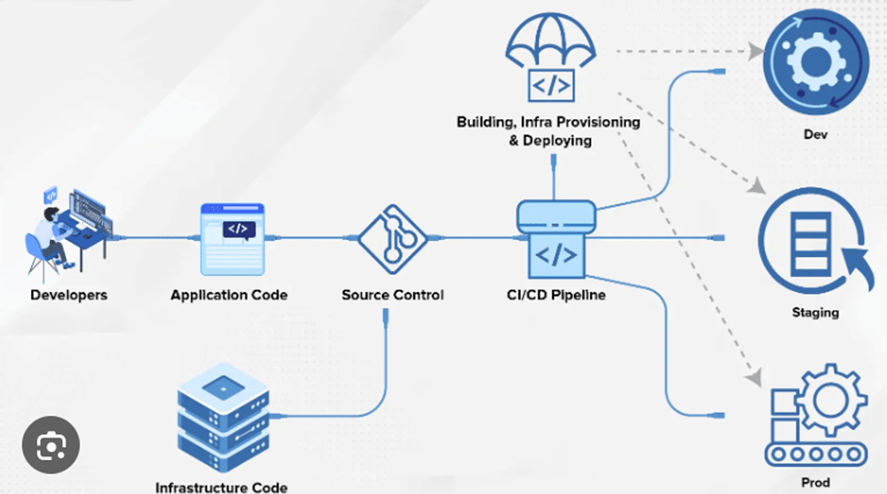
- Developers
They are the individuals or teams responsible for developing both the application and the infrastructure code.
- Application Code
This is the actual codebase for the application that will run on the infrastructure managed by IaC.
- Infrastructure Code
These are the scripts or definitions (configuration files) that specify the infrastructure setup written by developers, including servers, networks, and other resources. They allow the infrastructure to be managed as if it were software.
- Source Control
This is a version control system (like Git) that stores and tracks changes to both the application and the infrastructure code. This allows for versioning and collaboration among team members.
- CI/CD Pipeline
Stands for Continuous Integration/Continuous Deployment. This automated process takes the code from the source control, runs tests, builds the application, provisions the infrastructure, and deploys the application to it.
- Building, Infra Provisioning & Deploying
This is the stage where the infrastructure is created or updated based on the infrastructure code and the application is deployed. Typically, part of a Continuous Integration (CI) process, this involves compiling the application code into executable artifacts ready for deployment.
- Development/Stage/Production
These are the different environments where the application is deployed
- Development
Where new code is integrated and tested
- Staging
This is a pre-production environment that closely simulates the production environment. It is used for final testing before the application is released to production.
- Prod
Short for the production environment, this is where the application is live and accessible to end-users.
The flow depicted shows how code written by developers is committed to source control, automatically built and tested through the CI/CD pipeline, and then deployed to various environments following IaC practices. This ensures that infrastructure provisioning and management are automated, versioned, and repeatable, leading to more reliable deployments. The infrastructure in all environments is managed and provisioned according to the infrastructure code.
Stages in Infrastructure as a Code (IaC) security
- Development Phase
- Developers write the application code as well as the infrastructure code. The application code consists of the software that runs the business logic, while the infrastructure code defines the environment that the application runs on.
- Version Control
- Both the application code and the infrastructure code are stored in a version control system (like Git). This system allows for version tracking, collaborative work, and serves as the source of truth for the codebase.
- CI/CD Pipeline
- Once the codes are committed, the Continuous Integration/Continuous Deployment (CI/CD) pipeline is triggered. This pipeline includes steps like automated testing, building the application (compiling and packaging), and deploying the application alongside the infrastructure code.
- This CI/CD process may interact with a build server or services that manage these pipelines.
- Infrastructure Provisioning
- The infrastructure code is used to provision infrastructure either in the cloud or on-premises, depending on the organization’s architecture.
- An automation API or server takes the infrastructure code and applies it, which can involve orchestrating and configuring cloud resources or setting up on-premises servers and services.
- Management and Deployment
- The application code follows the CI/CD process to be deployed into various environments, Development, Stage, and Production.
- Development is where new features are tested, Stage is a pre-production environment mirroring the production setup, and Production is where the application goes live for the end-users.
- The infrastructure is also managed through the automation server, which can perform tasks like scaling, healing, and updating resources.
- Operational Phase
- Once deployed, the operational phase begins where the infrastructure and the application are monitored, and data is collected to ensure that they are functioning as intended and meeting performance and security standards.
- Monitoring and logging tools collect data from both cloud and on-premises infrastructure to provide insights into the system’s state and health.
In summary, the workflow encompasses the development of code, version control for collaboration and tracking, automated pipelines for integration and deployment, and the management of infrastructure across various environments, all while ensuring continuous monitoring and adjustment for security and reliability.
03. Real world example on usage or a user case scenario
Secure Cloud Infrastructure for Financial Services
A financial services company must ensure the highest levels of security and compliance due to the sensitive nature of their work with financial data. They turn to IaC to manage their cloud infrastructure securely.
- Scenario Setup
The company uses Terraform to define their cloud infrastructure, which includes multiple environments across development, staging, and production. Their infrastructure code specifies network configurations, server instances, and database services, along with compliance with financial industry regulations like PCI DSS and GDPR. [1]
- Version Control and Code Review
All infrastructure code is stored in a Git repository, with strict code review practices in place. Any changes to the infrastructure code undergo thorough reviews and automated security checks before being merged.
- Automated Compliance Scanning
Using tools like Chef InSpec or HashiCorp Sentinel, the company implements automated compliance scans. These tools are integrated into their CI/CD pipeline to continuously enforce security policies and compliance standards.
- Secrets Management
The company utilizes Vault by HashiCorp for secrets management, ensuring that all sensitive credentials, such as API keys and passwords, are encrypted and securely injected into the necessary parts of the infrastructure during provisioning. [1]
- Disaster Recovery
With IaC, the company has predefined disaster recovery plans as code. In an emergency, they can redeploy their entire cloud environment in a different region or cloud provider with minimal downtime. [2]
- Monitoring and Incident Response
Once the infrastructure is deployed, they use Splunk for monitoring and logging. If an anomaly is detected, the automation server can trigger a response, such as isolating affected systems or deploying additional security measures.
Through the implementation of IaC security practices, the financial services company can achieve rapid deployment while maintaining rigorous security and compliance, making their infrastructure both agile and secure.
E-commerce Platform Scalability
An e-commerce company wants to ensure that its platform remains secure, especially during high-traffic events like Black Friday or Cyber Monday. Using IaC, the company can,
- Automate Provisioning
Automatically provision additional servers in the cloud during peak times using predefined templates that include security configurations such as firewall rules, encryption, and access controls.
- Consistent Configuration
Ensure that each server deployed is configured exactly the same, reducing the risk of security breaches due to configuration drift or human error.
- Rollback Capabilities
Quickly rollback to a previous state if a new threat is detected or if a new update causes security vulnerabilities, thus minimizing downtime and exposure.
- Compliance Checks
Regularly run compliance as code checks to ensure the infrastructure meets industry security standards like PCI DSS for payment processing.
By integrating these practices, the company can manage large-scale infrastructure changes with confidence, knowing that security is embedded throughout the process.
Many organizations across various sectors utilize Infrastructure as Code (IaC) to bolster their security posture while managing complex infrastructure. Here are a few real-world instances
- Netflix
As a leader in the DevOps space, Netflix uses IaC for managing and scaling its massive cloud-based infrastructure, ensuring consistent security configurations across their vast fleet of servers.
- Etsy
This e-commerce company for handmade or vintage items and craft supplies is known for its innovative DevOps practices, leveraging IaC for automated and secure cloud configurations, aiding in their quick response to market demands. [1]
- Capital One
As a financial institution, Capital One utilizes IaC to maintain tight security measures in its cloud operations, adhering to stringent industry regulations and ensuring that its infrastructure meets compliance standards.
- Adobe
Adobe Systems uses IaC to manage its cloud resources securely and efficiently, enabling them to provide services that are robust, scalable, and secure.
- NASA’s Jet Propulsion Laboratory (JPL)
JPL uses IaC for managing cloud resources that handle immense data from various space missions, ensuring secure and compliant infrastructure automation. [2]
- HashiCorp
The company behind many IaC tools actively uses IaC to secure its own infrastructure and provides solutions for other companies to do the same with tools like Terraform and Vault.
- Nubank
One of the largest fintech companies in Latin America, Nubank leverages IaC for ensuring that all their cloud services are up to the security and compliance standards necessary for a financial institution.
- Atlassian
Known for their collaboration tools for teams, Atlassian uses IaC to maintain and scale their cloud services securely, enabling them to support millions of users worldwide. [1]
These instances illustrate how IaC is integral to companies for managing cloud infrastructure with a focus on security and compliance. By automating infrastructure deployment and management, these organizations enhance their ability to maintain secure, consistent, and reliable environments for their applications and services.
Top of Form
Applying security measures to Infrastructure as a code
The stages in Infrastructure as Code (IaC) security generally follow the lifecycle of IaC development and deployment while integrating security best practices throughout. Here’s an overview of these stages.
- Plan and Design
- Identify the security requirements for the infrastructure.
- Plan the architecture with security as a foundational element, including considerations for network segmentation, encryption, and access control.
- Write and Review Code
- Develop the IaC scripts using secure coding practices.
- Conduct thorough code reviews with a focus on security, potentially integrating automated security checks.
- Version Control and Baseline
- Check the IaC scripts into a version control system, such as Git, to maintain a history and audit trail.
- Establish a secure baseline configuration that all infrastructure should adhere to.
- Pre-Deployment Testing
- Run static analysis tools on the IaC scripts to detect potential security issues before deployment.
- Perform dynamic testing in a controlled environment to validate security configurations.
- Secure Deployment
- Use automated CI/CD pipelines to deploy infrastructure, integrating security checks as part of the deployment process.
- Ensure that the deployment process maintains the integrity of the IaC scripts and the confidentiality of any sensitive data.
- Post-Deployment Verification
- Verify that the deployed infrastructure matches the defined IaC and baseline security configuration.
- Perform compliance scanning to ensure the infrastructure adheres to regulatory and policy requirements.
- Monitoring and Logging
- Implement continuous monitoring solutions to detect and respond to security incidents in real-time.
- Collect logs for forensic analysis and to ensure ongoing compliance with security policies.
- Continuous Compliance and Remediation
- Regularly scan the environment to detect drift from the desired state.
- Automatically remediate any deviations to enforce compliance with security policies.
- Update and Adapt
- Keep the IaC scripts up to date with the latest security patches and best practices.
- Adapt the IaC to evolving threats and changing security requirements.
- Documentation and Training
- Document all processes and maintain updated records of security practices and configurations.
- Train the team on security best practices specific to IaC and the tools in use.
By integrating security throughout these stages, organizations can ensure that their IaC practices support a strong security posture that is proactive, adaptable, and aligned with their overall risk management strategy.
How to ensure IaC security
Ensuring Infrastructure as Code (IaC) security involves several best practices and strategies throughout the development and management lifecycle of infrastructure.
- Secure Coding Practices
Write IaC scripts with security in mind, following best practices for secure coding. Avoid hardcoding sensitive data and ensure that the code is readable and maintainable.
- Version Control
Use version control systems like Git for all IaC scripts, which provides an audit trail for changes and helps in tracking and reverting modifications if needed.
- Code Review and Pair Programming
Implement rigorous code review processes to catch potential security issues. Pair programming can also help share knowledge and ensure code quality.
- Static Code Analysis
Integrate static code analysis tools to automatically review the IaC scripts for common security issues and misconfigurations before deployment. [3]
- Dynamic Security Scanning
Perform dynamic scans of the infrastructure once it is deployed to identify runtime security issues that static analysis may not catch.
- Automated Compliance Scanning
Use tools that can compare your IaC scripts against compliance benchmarks and standards, ensuring that your infrastructure adheres to required regulations and best practices. [3]
- Least Privilege Access
Ensure that IaC scripts enforce the principle of least privilege in infrastructure configurations, granting only the necessary access rights required for each component.
- Secrets Management
Utilize a secrets management tool to handle sensitive data such as passwords, tokens, and keys, rather than embedding them directly in the IaC scripts.
- Immutable Infrastructure
Adopt an immutable infrastructure approach where changes are made by replacing the infrastructure rather than modifying it in place, which can help prevent drift and reduce the attack surface.
- Change Management
Use a change management system to approve and log all changes to the infrastructure, providing visibility and accountability.
- Drift Detection
Regularly check for configuration drift — unintended changes to infrastructure — and rectify it to maintain a known, secure state.
- Continuous Monitoring
Implement continuous monitoring solutions to detect and respond to security incidents in real time.
- Disaster Recovery Planning
Have a disaster recovery plan in place that leverages IaC for quick recovery in case of security breaches or other disasters.
- Education and Awareness
Train the team on the security aspects of IaC, including recognizing security threats and understanding the importance of security in automated environments.
- Regular Auditing
Regularly audit your infrastructure and IaC scripts for security vulnerabilities and compliance with the latest security policies and standards.
By systematically incorporating these practices into your IaC workflows, you can significantly enhance the security of your infrastructure automation processes.
Pros of Infrastructure as Code (IaC) Security
- Consistency and Standardization
IaC allows for the consistent deployment of environments, reducing the risk of human error and the inconsistencies that can create security vulnerabilities.
- Automated Compliance
It can integrate compliance as code, ensuring that infrastructure automatically adheres to specified compliance policies and standards, making it easier to maintain compliance across the board.
- Version Control and History
Changes to the infrastructure are tracked through version control systems, providing an audit trail for all changes, and facilitating rollbacks when necessary. [3]
- Rapid Response
IaC can quickly respond to security threats by updating code and re-deploying the infrastructure as needed.
- Cost-Effective
Reduces the costs associated with manual setup and maintenance of the infrastructure, and allows for quicker remediation of issues, which can be expensive if left unresolved.
- Scalability
Supports the management of large-scale infrastructure with less effort than traditional methods, allowing security measures to scale the infrastructure.
- Documentation
Acts as a form of documentation for the infrastructure, which is beneficial for security audits and compliance checks.
Cons of Infrastructure as Code (IaC) Security
- Complexity
The learning curve can be steep, and setting up an IaC environment with robust security can be complex, especially for teams new to the concept.
- Tooling Integration
Requires integration with various tools for comprehensive security, and these integrations can be complex and may introduce their own security challenges.
- Initial Setup Cost
While cost-effective in the long run, initial setup for IaC can be resource-intensive, requiring investment in both time and capital. [3]
- Script Vulnerabilities
IaC scripts can themselves be a target for attackers. If not managed securely, they can become a vector for security breaches.
- Drift Detection
There is a risk of configuration drift where the actual state diverges from the state defined in the code, which can lead to security vulnerabilities if not detected and managed properly.
- Dependence on Expertise
Secure IaC implementation depends on having skilled personnel who understand both the infrastructure and security implications, which can be a challenge in terms of staffing and knowledge management.
- Automation Risks
Automated provisioning and management can propagate errors or vulnerabilities quickly across the entire infrastructure if the IaC scripts are not properly designed and tested.
Balancing these pros and cons is essential for any organization implementing IaC to ensure that their infrastructure is as secure and efficient as possible.
Conclusion.
Infrastructure as Code (IaC) is revolutionizing how organizations manage and secure their IT infrastructure. By codifying infrastructure setups, IaC provides a more efficient, consistent, and secure approach to infrastructure management, critical in today’s rapidly evolving digital landscape.
Key Takeaways
- Automated and Consistent
IaC automates infrastructure provisioning, ensuring consistent configurations and reducing the risk of human error.
- Version Control Integration
With IaC, infrastructure changes are tracked via version control systems, providing an audit trail and facilitating easy rollbacks.
- Security From the Start
Security is embedded in every stage, from planning and code development to deployment and monitoring.
- Real-Time Monitoring
Continuous monitoring enables immediate detection and response to potential security threats.
- Immutable Infrastructure
This approach minimizes risks by replacing infrastructure instead of altering it, ensuring a consistent and secure state.
- Compliance and Scalability
IaC ensures that infrastructure adheres to compliance standards and scales securely with organizational needs.
Challenges and Considerations
- Complexity and Expertise
While powerful, IaC requires specialized knowledge and careful planning to avoid potential pitfalls like script vulnerabilities and configuration drift.
- Investment in Tooling and Training
Effective IaC security demands an investment in the right tools and training for personnel to manage these systems effectively.
Future of IaC Security
- As technology evolves, IaC is poised to become even more integral to infrastructure management, with continuous improvements in automation, compliance scanning, and threat detection. [5]
- The key to success lies in maintaining a balance between the automation benefits and the need for rigorous security controls, ensuring that IaC not only simplifies infrastructure management but also elevates the overall security posture of organizations.
In summary, IaC represents a significant step forward in managing and securing IT infrastructure, offering scalability, consistency, and enhanced security. However, its effective implementation requires a combination of robust tools, skilled personnel, and continuous monitoring to safeguard against evolving cyber threats.Top of Form
References
| [1] | C. W. Team, “What is Infrastructure as Code Security (IaC) – Best Practices Guide in 2024,” 23 January 2024. [Online]. Available: https://cybersecuritynews.com/infrastructure-as-code-security/[Accessed:20-Mar-2024] |
| [2] | 1. M. G. D. A. T. F. P. Michele Guerriero, “Adoption, Support, and Challenges of Infrastructure-as-Code: Insights from Industry,” p. 10, 2023.[Online] Available: https://ieeexplore.ieee.org/document/8919181[Accessed:25-Mar-2024] doi: 10.1109/ICSME.2019.00092 |
| [3] | L. G. Payton O’Neal, “IaC Security,” Dzone, 29 June 2021. [Online].Available: https://dzone.com/refcardz/iac-security-1[Accessed:25-Mar-2024] |
| [4] | O. Murphy, , Adoption of Infrastructure as Code (IaC) in Real World, 2022. [Online] Available: https://www.theseus.fi/bitstream/handle/10024/786729/Thesis_Murphy_Olga_YTS20K1.pdf?sequence=2[Accessed:30-Mar-2024] |
| [5] | I. A.-C. U. L. M. P.-A. Tiago Espinha Gasiba, “Raising Security Awareness of Cloud Deployments using Infrastructure as Code through CyberSecurity Challenges,” p. 09, 07 August 2021. [Online] Available: https://www.researchgate.net/publication/353937690_Raising_Security_Awareness_of_Cloud_Deployments_using_Infrastructure_as_Code_through_CyberSecurity_Challenges[Accessed:30-Mar-2024] doi: 10.1145/3465481.3470030 |

Leave a comment